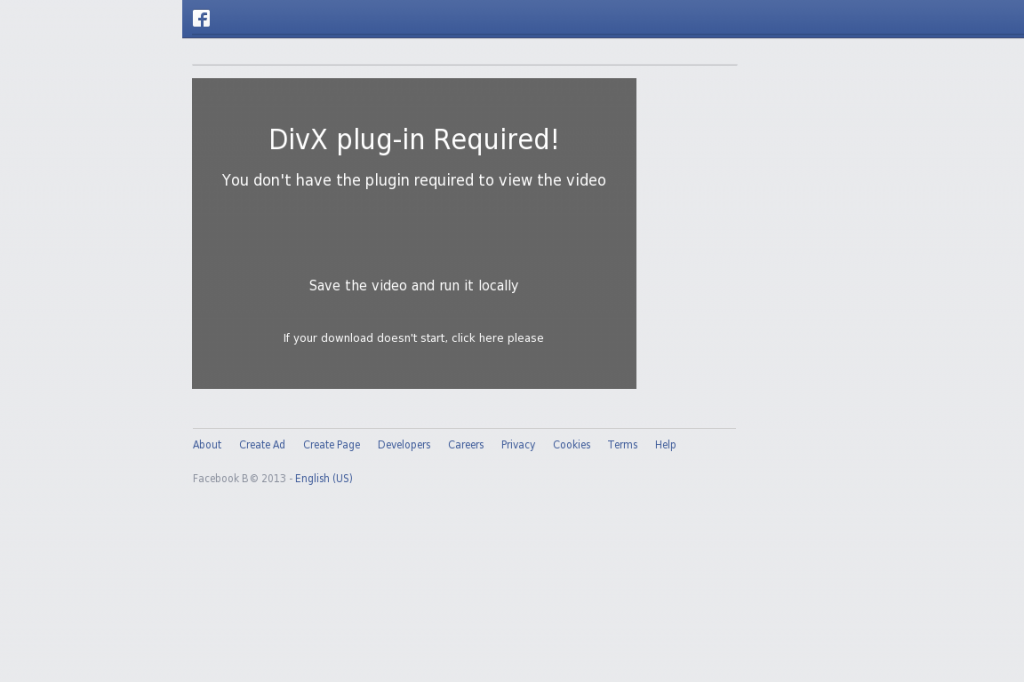
Our sensors just picked up
an interesting Web site infection,
this time affecting a Web server belonging to the Turkish government,
where the cybercriminals behind the campaign have uploaded a
malware-serving fake ‘DivX plug-in Required!” Facebook-themed Web page.
Once socially engineered users execute the malware variant, their PCs
automatically join the botnet operated by the cybercriminals behind the
campaign.
Sample screenshot of the fake DivX, Facebook-themed page uploaded on the compromised Web server:
 Compromised URL: hxxp://www.manisahem.gov.tr/giorgia.html
The malware’s download URL: hxxp://hyfcst.best.volyn.ua:80/dlimage11.php
Compromised URL: hxxp://www.manisahem.gov.tr/giorgia.html
The malware’s download URL: hxxp://hyfcst.best.volyn.ua:80/dlimage11.php – 103.246.115.238
Detection rate for the malicious variant:
MD5: adc9cafbd4e2aa91e4aa75e10a948213 – detected by 3 out of 48 antivirus scanners as Heuristic.LooksLike.Win32.Suspicious.J!89
The following malicious sub-domains are also known to have responded to the same IP (103.246.115.238):
qpqaaa.best.volyn.ua
ohbkaa.best.volyn.ua
wknqba.best.volyn.ua
wnewca.best.volyn.ua
arlrda.best.volyn.ua
umozea.best.volyn.ua
thkbga.best.volyn.ua
hibfha.best.volyn.ua
idktia.best.volyn.ua
dgplka.best.volyn.ua
cdqdqa.best.volyn.ua
tgxsqa.best.volyn.ua
cozeva.best.volyn.ua
fwomva.best.volyn.ua
sekbwa.best.volyn.ua
goqgwa.best.volyn.ua
bcrgwa.best.volyn.ua
bekpwa.best.volyn.ua
cflwwa.best.volyn.ua
mrfbya.best.volyn.ua
ldstya.best.volyn.ua
bspzab.best.volyn.ua
cctmcb.best.volyn.ua
knafdb.best.volyn.ua
egzbeb.best.volyn.ua
ixlyeb.best.volyn.ua
ynozfb.best.volyn.ua
wqzegb.best.volyn.ua
xzckhb.best.volyn.ua
ddznib.best.volyn.ua
hdxoib.best.volyn.ua
rqaakb.best.volyn.ua
ofmakb.best.volyn.ua
xpirlb.best.volyn.ua
agoylb.best.volyn.ua
higsnb.best.volyn.ua
qhuwnb.best.volyn.ua
ldkfob.best.volyn.ua
faawtb.best.volyn.ua
hdwdub.best.volyn.ua
skerub.best.volyn.ua
vxefwb.best.volyn.ua
aspywb.best.volyn.ua
xstbyb.best.volyn.ua
qssdac.best.volyn.ua
vfcxac.best.volyn.ua
ninwcc.best.volyn.ua
bboyhc.best.volyn.ua
iaiomc.best.volyn.ua
emsvmc.best.volyn.ua
bzxypc.best.volyn.ua
rkezqc.best.volyn.ua
ycecrc.best.volyn.ua
yzzorc.best.volyn.ua
lmstrc.best.volyn.ua
vmrusc.best.volyn.ua
yukbtc.best.volyn.ua
mpowxc.best.volyn.ua
tesgdd.best.volyn.ua
wuvwed.best.volyn.ua
pxrpgd.best.volyn.ua
qiyphd.best.volyn.ua
oicmkd.best.volyn.ua
ofslld.best.volyn.ua
okrfnd.best.volyn.ua
ibbvod.best.volyn.ua
xokmpd.best.volyn.ua
tbsnpd.best.volyn.ua
ygfbvd.best.volyn.ua
gimgyd.best.volyn.ua
wbddce.best.volyn.ua
tzhmce.best.volyn.ua
wfgwde.best.volyn.ua
grndie.best.volyn.ua
aqxlke.best.volyn.ua
eviime.best.volyn.ua
ilymre.best.volyn.ua
ywcure.best.volyn.ua
szigse.best.volyn.ua
flqfue.best.volyn.ua
ixtaxe.best.volyn.ua
gfdxxe.best.volyn.ua
swscye.best.volyn.ua
kgemze.best.volyn.ua
awdfcf.best.volyn.ua
cbiief.best.volyn.ua
osorff.best.volyn.ua
qerohf.best.volyn.ua
arwbif.best.volyn.ua
apgmlf.best.volyn.ua
lfnasf.best.volyn.ua
bayxwf.best.volyn.ua
utxzxf.best.volyn.ua
sqhhzf.best.volyn.ua
bcpagg.best.volyn.ua
gyyfhg.best.volyn.ua
xwoqlg.best.volyn.ua
abnrog.best.volyn.ua
dhgypg.best.volyn.ua
xytwqg.best.volyn.ua
svzyqg.best.volyn.ua
cxhstg.best.volyn.ua
mbcwtg.best.volyn.ua
fgrgvg.best.volyn.ua
rpkkwg.best.volyn.ua
bghuwg.best.volyn.ua
neqmxg.best.volyn.ua
dlylah.best.volyn.ua
ozoceh.best.volyn.ua
xufcgh.best.volyn.ua
nixblh.best.volyn.ua
yyhflh.best.volyn.ua
rimulh.best.volyn.ua
oewgmh.best.volyn.ua
eacnmh.best.volyn.ua
gdvvnh.best.volyn.ua
voolph.best.volyn.ua
bqgrph.best.volyn.ua
pzhtsh.best.volyn.ua
kydwsh.best.volyn.ua
zviath.best.volyn.ua
pclpth.best.volyn.ua
vyeuvh.best.volyn.ua
hcdgdi.best.volyn.ua
ybmwei.best.volyn.ua
lizxei.best.volyn.ua
ehczei.best.volyn.ua
ahmkfi.best.volyn.ua
fwtihi.best.volyn.ua
ttlqhi.best.volyn.ua
phexhi.best.volyn.ua
rnhqli.best.volyn.ua
hfibni.best.volyn.ua
ehicoi.best.volyn.ua
bxogoi.best.volyn.ua
ruiyri.best.volyn.ua
ozeqsi.best.volyn.ua
uinzsi.best.volyn.ua
xdwnui.best.volyn.ua
uikoui.best.volyn.ua
zmglvi.best.volyn.ua
reewzi.best.volyn.ua
ocbvak.best.volyn.ua
bbqnck.best.volyn.ua
dawrdk.best.volyn.ua
dwtbek.best.volyn.ua
rcteek.best.volyn.ua
encoek.best.volyn.ua
kvnvek.best.volyn.ua
knwrhk.best.volyn.ua
svzuik.best.volyn.ua
ofwclk.best.volyn.ua
khielk.best.volyn.ua
rbocmk.best.volyn.ua
bbssok.best.volyn.ua
ovutok.best.volyn.ua
egfppk.best.volyn.ua
pgwtpk.best.volyn.ua
kbpupk.best.volyn.ua
rdhotk.best.volyn.ua
phnkvk.best.volyn.ua
wvkswk.best.volyn.ua
ccsixk.best.volyn.ua
lmepxk.best.volyn.ua
uiicyk.best.volyn.ua
ytpzyk.best.volyn.ua
nyrmal.best.volyn.ua
hyqiel.best.volyn.ua
fccvll.best.volyn.ua
napyll.best.volyn.ua
buubpl.best.volyn.ua
mowcql.best.volyn.ua
grzqsl.best.volyn.ua
zezotl.best.volyn.ua
drwkxl.best.volyn.ua
ltkiyl.best.volyn.ua
kdnpyl.best.volyn.ua
kzgxzl.best.volyn.ua
ifltbm.best.volyn.ua
codhgm.best.volyn.ua
baxtgm.best.volyn.ua
fixygm.best.volyn.ua
dfrtkm.best.volyn.ua
cpialm.best.volyn.ua
gnyylm.best.volyn.ua
rashmm.best.volyn.ua
olpwmm.best.volyn.ua
ndoiom.best.volyn.ua
ufpzom.best.volyn.ua
kovoqm.best.volyn.ua
qzwysm.best.volyn.ua
xzftum.best.volyn.ua
yvugvm.best.volyn.ua
vahqvm.best.volyn.ua
hclhwm.best.volyn.ua
exylzm.best.volyn.ua
bginbn.best.volyn.ua
ygyzbn.best.volyn.ua
opxkcn.best.volyn.ua
wxlqdn.best.volyn.ua
We’re also aware of the following malicious MD5s that are known to have been downloaded from the same IP (103.246.115.238):
MD5: 4aacf36cafbd8db3558f523ddc8c90e5
MD5: 3dff37ee5d6e3a1bc6f37c58ac748821
MD5: 4ce289a8e3b4dd374221d2b56f921f6d
MD5: e3f8456d5188fd03f202bfe112d3353d
MD5: 9698be7d8551cb89a95ce285c84c46b1
MD5: be8c528a6bff6668093e9aabe0634197
MD5: 48bcc188a4d6a2c70ee495a7742b68b8
MD5: c0f3501b63935add01a6b4aa458a01b7
MD5: 10c32d95367bb9ab2928390ff8689a26
MD5: 39b59bda3c65989b9288f10789779e96
MD5: aa7dc576d1fe71f18374f9b4ae6869fa
MD5: 00bdd194328c2fe873260970da585d84
MD5: 3ad96ccf8e7c5089b80232529ffe8f62
MD5: 1f18b45b25dd50adf163d91481c851cf
MD5: 9577c1b005673e1406da41fb07e914bb
MD5: 19e31123c1ccc072c257347bba220f0e
MD5: b60ca81cec260d44025c2b0374364272
MD5: 0a960df88c2d27d0d4cc27544011fbb0
MD5: 7d14dcfd00f364c788ba51c6c2fc6bdd
Once executed, the original sample MD5: adc9cafbd4e2aa91e4aa75e10a948213 phones back to:
103.9.150.244/tsone/vowet11.dat?wv=51&bt=32
The following malicious subdomains are also known to have responded to the same IP (103.9.150.244):
abkwnb.best.lt.ua
abnrog.best.volyn.ua
acggdk.best.lt.ua
acuhpw.best.lt.ua
adasqo.best.lt.ua
adybuq.best.lt.ua
afvvkz.best.lt.ua
aiikit.best.volyn.ua
aixxap.best.lt.ua
akzoze.best.lt.ua
amnrks.best.volyn.ua
amsbud.best.volyn.ua
aoimih.best.volyn.ua
aqbrpz.best.lt.ua
arsrra.best.lt.ua
asksxw.best.lt.ua
aszhet.best.lt.ua
atfvmk.best.lt.ua
2ayrzwv.best.lt.ua
azcgrd.best.lt.ua
We’re also aware of the following malicious MD5s that are known to have phoned back to the same IP (103.9.150.244):
MD5: 0e27df7a010338d554dba932b94cb11e
MD5: a6e52ca88a4cd80eb39989090d246631
MD5: ab0d8f81b65e5288dd6004f2f20280fd
MD5: e1bda5b01d1ad8c0f48177cd6398b15f
MD5: b2a381fbc544fe69250ad287b55f435b
MD5: 052ae7410594c5c0522afd89eccb85a7
MD5: ddfac94608f8b6c0acfadc7a36323fe6
MD5: 052ae7410594c5c0522afd89eccb85a7
MD5: ddfac94608f8b6c0acfadc7a36323fe6
MD5: 9325e2dddded560c2e7a214eb920f9ea
MD5: 56aaea2b443ea8c9cea248e64d645305
MD5: 4e0bff23a95e8d02800fecbac184cd5f
MD5: 704c5b12247826cf111b1a0fc3678766
MD5: c5fb893b401152e625565605d85a6b7d
MD5: 540f19ff5350e08eff2c5c4bada1f01f
MD5: 8db8c55983125113e472d7dd6a47bd43
MD5: 7c4d4e56f1a9ceb096df49da42cc00ed