After traveling around the past few months in various countries it
looks like getting rid of Windows XP is going to take quite a while. It
is probably due to the fact that it has expired that I noticed it more
than usual, but XP is certainly everywhere. You see it at airports on
display boards, Point of Sale systems. In one overseas country the
computers in customs as well as the railway displays and control systems
and hospitals.
Having obsolete operating systems in a corporate environment is bad
enough, there are still many organisations that utilise XP internally.
However as part of critical infrastructure it worries me slightly more.
Now most of us can't do much outside of our little sphere of
influence, but it is time for the operating system to go.
So if junior needs something to do over the next few weeks set them a
challenge. Identify all remaining XP devices connected to the network.
Categorise them into real XP and embedded XP ( Still some support
available for those). Then develop a strategy to get rid of them.
If getting rid of them is not an option and there will those of you
in that situation, at least look for ways of protecting them a bit
better. Consider network segmentation, application whitelisting,
endpoint solutions (some will still work on XP). As an absolute minimum
at least know where they are and how they are being used.
Seek, identify and remove away.
Information Security, Ethical Hacking, website Security, Database Security, IT Audit and Compliance, Security news, Programming, Linux and Security.
Wednesday, 18 June 2014
B.C. court ruling orders Google to block sites worldwide
In an unprecedented ruling, a B.C. court has ordered Google Inc.
to block a group of websites from its worldwide search engine – a
decision raising questions over how far one country’s courts can exert
their power over the borderless Internet.
The temporary injunction, issued by B.C. Supreme Court Justice Lauri Ann Fenlon on June 13, came despite arguments from Google’s lawyers that Canada’s courts did not have the jurisdiction to tell Google, based in Mountain View, Calif., to block access to the websites anywhere in the world.
In an e-mailed statement, Google said it was disappointed in the decision and said it would launch an appeal. It declined requests for an interview.
Legal observers say the court order raises broader questions – questions increasingly dogging judges around the world – about just whose rules should prevail as the Internet continues to blur or erase national borders.
It follows a landmark decision by the European Union Court of Justice on the so-called “right to be forgotten” that forces Google to take down certain information about private individuals if asked.
The B.C. injunction, which orders Google to comply within 14 days, is part of a court fight launched by Burnaby, B.C.-based Equustek Solutions Inc., which makes and sells complex industrial networking devices.
According to the ruling, the company alleges that a group of former associates stole its trade secrets in order to manufacture competing products, which they continue to sell through a network of websites, in “flagrant” defiance of numerous previous court orders.
Google’s current procedure would allow it to block search results for offending website addresses on its Canadian website, Google.ca. But most of the defendants’ sales occur outside Canada, the ruling says; even within Canada, the defendants simply switched URLs, turning the exercise into “an endless game of ‘whac-a-mole.’”
In her ruling, Justice Fenlon determined the B.C. court had jurisdiction over Google, noting the company sells ads in British Columbia and uses its search technology to target those ads to British Columbians. She granted the plaintiffs an injunction that she said no Canadian court had granted before.
“Google is an innocent bystander but it is unwittingly facilitating the defendants’ ongoing breaches of this Court’s orders,” her ruling reads.
“The Court must adapt to the reality of e-commerce with its potential for abuse by those who would take the property of others and sell it through the borderless electronic web of the internet,” she writes.
Canadian courts, and others around the world, have been increasingly extending their reach across borders in a variety of areas. And Canadian courts have in the past issued orders affecting people or entities outside its borders, such as injunctions demanding the freezing of assets.
But University of Ottawa law professor Michael Geist slammed the recent Google decision in a blog post on Tuesday, warning that it could lead to other countries demanding Google censor content worldwide, putting free speech at risk. “While the court does not grapple with this possibility, what happens if a Russian court orders Google to remove gay and lesbian sites from its database? Or if Iran orders it remove Israeli sites from the database?”
In an interview, Prof. Geist said he agrees the court has jurisdiction over Google but disagrees that it should have the power to issue an essentially global injunction: “That seems to be to be a very dangerous overreach.”
Robert Fleming, the lawyer for the Vancouver plaintiffs who won the injunction against Google, said no court elsewhere in the world would recognize such extreme orders against Google as those Prof. Geist suggests. Unlike Prof. Geist’s hypothetical cases, Mr. Fleming said, his case is an intellectual property dispute over which U.S. and other courts would clearly recognize the B.C. court has jurisdiction – not a question of free-speech.
And in his case, he said, the main defendant, Morgan Jack, has repeatedly breached previous court orders and has failed to show up for court proceedings. According to court documents, Mr. Jack has “disappeared,” although his websites allegedly continue to operate.
This has forced Mr. Fleming’s clients to take the steps they have against Google. “Things happen so quickly and on the Internet they are so borderless, the courts have to be able to adapt,” he said.
The temporary injunction, issued by B.C. Supreme Court Justice Lauri Ann Fenlon on June 13, came despite arguments from Google’s lawyers that Canada’s courts did not have the jurisdiction to tell Google, based in Mountain View, Calif., to block access to the websites anywhere in the world.
In an e-mailed statement, Google said it was disappointed in the decision and said it would launch an appeal. It declined requests for an interview.
Legal observers say the court order raises broader questions – questions increasingly dogging judges around the world – about just whose rules should prevail as the Internet continues to blur or erase national borders.
It follows a landmark decision by the European Union Court of Justice on the so-called “right to be forgotten” that forces Google to take down certain information about private individuals if asked.
The B.C. injunction, which orders Google to comply within 14 days, is part of a court fight launched by Burnaby, B.C.-based Equustek Solutions Inc., which makes and sells complex industrial networking devices.
According to the ruling, the company alleges that a group of former associates stole its trade secrets in order to manufacture competing products, which they continue to sell through a network of websites, in “flagrant” defiance of numerous previous court orders.
Google’s current procedure would allow it to block search results for offending website addresses on its Canadian website, Google.ca. But most of the defendants’ sales occur outside Canada, the ruling says; even within Canada, the defendants simply switched URLs, turning the exercise into “an endless game of ‘whac-a-mole.’”
In her ruling, Justice Fenlon determined the B.C. court had jurisdiction over Google, noting the company sells ads in British Columbia and uses its search technology to target those ads to British Columbians. She granted the plaintiffs an injunction that she said no Canadian court had granted before.
“Google is an innocent bystander but it is unwittingly facilitating the defendants’ ongoing breaches of this Court’s orders,” her ruling reads.
“The Court must adapt to the reality of e-commerce with its potential for abuse by those who would take the property of others and sell it through the borderless electronic web of the internet,” she writes.
Canadian courts, and others around the world, have been increasingly extending their reach across borders in a variety of areas. And Canadian courts have in the past issued orders affecting people or entities outside its borders, such as injunctions demanding the freezing of assets.
But University of Ottawa law professor Michael Geist slammed the recent Google decision in a blog post on Tuesday, warning that it could lead to other countries demanding Google censor content worldwide, putting free speech at risk. “While the court does not grapple with this possibility, what happens if a Russian court orders Google to remove gay and lesbian sites from its database? Or if Iran orders it remove Israeli sites from the database?”
In an interview, Prof. Geist said he agrees the court has jurisdiction over Google but disagrees that it should have the power to issue an essentially global injunction: “That seems to be to be a very dangerous overreach.”
Robert Fleming, the lawyer for the Vancouver plaintiffs who won the injunction against Google, said no court elsewhere in the world would recognize such extreme orders against Google as those Prof. Geist suggests. Unlike Prof. Geist’s hypothetical cases, Mr. Fleming said, his case is an intellectual property dispute over which U.S. and other courts would clearly recognize the B.C. court has jurisdiction – not a question of free-speech.
And in his case, he said, the main defendant, Morgan Jack, has repeatedly breached previous court orders and has failed to show up for court proceedings. According to court documents, Mr. Jack has “disappeared,” although his websites allegedly continue to operate.
This has forced Mr. Fleming’s clients to take the steps they have against Google. “Things happen so quickly and on the Internet they are so borderless, the courts have to be able to adapt,” he said.
SHODAN – Expose Online Devices Wind Turbines, Power Plants & More!
SHODAN is a search engine that lets you find specific computers (routers, servers, etc.) using a variety of filters. Some have also described it as a public port scan directory or a search engine of banners.
Web search engines, such as Google and Bing, are great for finding websites. But what if you’re interested in finding computers running a certain piece of software (such as Apache)? Or if you want to know which version of Microsoft IIS is the most popular? Or you want to see how many anonymous FTP servers there are? Maybe a new vulnerability came out and you want to see how many hosts it could infect? Traditional web search engines don’t let you answer those questions.
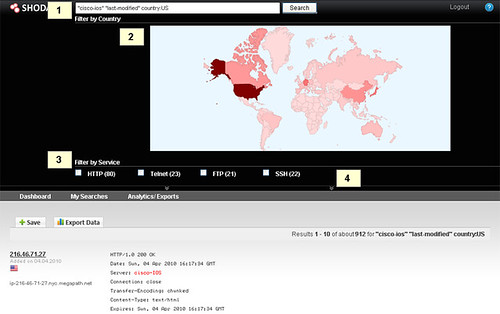 So what does SHODAN index then? Good question.
The bulk of the data is taken from ‘banners’, which are meta-data the
server sends back to the client. This can be information about the server software,
what options the service supports, a welcome message or anything else
that the client would like to know before interacting with the server.
For example, following is a FTP banner:
So what does SHODAN index then? Good question.
The bulk of the data is taken from ‘banners’, which are meta-data the
server sends back to the client. This can be information about the server software,
what options the service supports, a welcome message or anything else
that the client would like to know before interacting with the server.
For example, following is a FTP banner:
This tells us a potential name of the server (kcg.cz), the type of
FTP server (Solaris ftpd) and its version (6.00LS). For HTTP a banner
looks like:
This can be used to find all sorts of interesting things like
Webcams, routers, power plants, iPhones, wind turbines, refrigerators –
basically anything connected to the internet that has a banner that
identifies what it is.
There is an API service as well if you want to build an app around the data in the Shodan database at https://developer.shodan.io/. The Shodan API is the easiest way to provide users of your tool access to the Shodan data. The API provides access to all of the search features, allowing you to get exactly the information you want. There are libraries for Python, Ruby & NodeJS.
You can get started with Shodan here – http://www.shodanhq.com/
Web search engines, such as Google and Bing, are great for finding websites. But what if you’re interested in finding computers running a certain piece of software (such as Apache)? Or if you want to know which version of Microsoft IIS is the most popular? Or you want to see how many anonymous FTP servers there are? Maybe a new vulnerability came out and you want to see how many hosts it could infect? Traditional web search engines don’t let you answer those questions.

|
1
|
220kcg.cz FTP server(Version6.00LS)ready.
|
|
1
2
3
4
5
6
7
8
|
HTTP/1.0200OK
Date:Tue,16Feb201010:03:04GMT
Server:Apache/1.3.26(Unix)AuthMySQL/2.20PHP/4.1.2mod_gzip/1.3.19.1amod_ssl/2.8.9OpenSSL/0.9.6g
Last-Modified:Wed,01Jul199808:51:04GMT
ETag:“135074-61-3599f878″
Accept-Ranges:bytes
Content-Length:97
Content-Type:text/html
|
There is an API service as well if you want to build an app around the data in the Shodan database at https://developer.shodan.io/. The Shodan API is the easiest way to provide users of your tool access to the Shodan data. The API provides access to all of the search features, allowing you to get exactly the information you want. There are libraries for Python, Ruby & NodeJS.
You can get started with Shodan here – http://www.shodanhq.com/
People will happily run malware if paid ONE CENT – new study
Security white hats, despair: users will run dodgy executables if they are paid as little as one cent.
Even more would allow their computers to become infected by botnet software nasties if the price was increased to five or 10 cents. Offer a whole dollar and you'll secure a herd of willing internet slaves.
The demoralising findings come from a study lead by Nicolas Christin, research professor at Carnegie Mellon University's CyLab which baited users with a benign Windows executable sold to users under the guise of contributing to a (fictitious) study.
It was downloaded 1,714 times and 965 users actually ran the code. The application ran a timer simulating an hour's computational tasks after which a token for payment would be generated.
The researchers collected information on user machines discovering that many of the predominantly US and Indian user machines were already infected with malware despite having security systems installed, and were happy to click past Windows' User Access Control warning prompts.
The presence of malware actually increased on machines running the latest patches and infosec tools in what was described as an indication of users' false sense of security.
Users completing the tasks told a subsequent questionnaire they were conscious of security risks leading to the conclusion that users were happy to give up control of their machines for a pittance provided compute power was not impacted.
It was fantastic news for bot owners who could offer payment in exchange for exclusive control of more stable zombie machines: such a model was dubbed a "Fair Trade Botnet".
"We demonstrate that, far from being consistent with their stated preferences, in practice, users actually do not attach any significant economic value to the security of their systems," research quartet Nicolas Christina, Serge Egelmanb, Timothy Vidasc, and Jens Grossklags wrote in a paper titled It’s All About The Benjamins (PDF).
"While ignorance could explain this state of affairs, we show that the reality is much worse, as some users readily turn a blind eye to questionable activities occurring on their systems, as long as they can themselves make a modest profit out of it," the researchers write, adding that "...many users seem to be content ignoring possible security compromises as long as the compromised state does not noticeably impact the performance of the machine."
The tool was reposted to Amazon's Mechanical Turk every week for five weeks with the price paid for the work increasing every seven days from $0.01 to $0.05, $0.10, $0.50, and finally $1.00. Users could not participate if they had already done so in prior weeks.
More users were expectantly willing to run the potential bot trojan at $1, but still 22 per cent of the total sucker count played for one cent.
Seventeen users won a gold star by running the executable in a virtual machine.
"This raises questions about the effectiveness of well known security advice when competing against the smallest of incentives," the researchers wrote.
Readers can listen to a podcast of Christin discussing the work at the 2014 Workshop on Security and Human Behaviour.
Even more would allow their computers to become infected by botnet software nasties if the price was increased to five or 10 cents. Offer a whole dollar and you'll secure a herd of willing internet slaves.
The demoralising findings come from a study lead by Nicolas Christin, research professor at Carnegie Mellon University's CyLab which baited users with a benign Windows executable sold to users under the guise of contributing to a (fictitious) study.
It was downloaded 1,714 times and 965 users actually ran the code. The application ran a timer simulating an hour's computational tasks after which a token for payment would be generated.
The researchers collected information on user machines discovering that many of the predominantly US and Indian user machines were already infected with malware despite having security systems installed, and were happy to click past Windows' User Access Control warning prompts.
The presence of malware actually increased on machines running the latest patches and infosec tools in what was described as an indication of users' false sense of security.
Users completing the tasks told a subsequent questionnaire they were conscious of security risks leading to the conclusion that users were happy to give up control of their machines for a pittance provided compute power was not impacted.
It was fantastic news for bot owners who could offer payment in exchange for exclusive control of more stable zombie machines: such a model was dubbed a "Fair Trade Botnet".
"We demonstrate that, far from being consistent with their stated preferences, in practice, users actually do not attach any significant economic value to the security of their systems," research quartet Nicolas Christina, Serge Egelmanb, Timothy Vidasc, and Jens Grossklags wrote in a paper titled It’s All About The Benjamins (PDF).
"While ignorance could explain this state of affairs, we show that the reality is much worse, as some users readily turn a blind eye to questionable activities occurring on their systems, as long as they can themselves make a modest profit out of it," the researchers write, adding that "...many users seem to be content ignoring possible security compromises as long as the compromised state does not noticeably impact the performance of the machine."
The tool was reposted to Amazon's Mechanical Turk every week for five weeks with the price paid for the work increasing every seven days from $0.01 to $0.05, $0.10, $0.50, and finally $1.00. Users could not participate if they had already done so in prior weeks.
More users were expectantly willing to run the potential bot trojan at $1, but still 22 per cent of the total sucker count played for one cent.
Seventeen users won a gold star by running the executable in a virtual machine.
"This raises questions about the effectiveness of well known security advice when competing against the smallest of incentives," the researchers wrote.
Readers can listen to a podcast of Christin discussing the work at the 2014 Workshop on Security and Human Behaviour.
FTC seeks DEFCON help to finger illegal robocallers
The Federal Trade Commission is to host a cash competition at this
year's DEFCON hacking conference in Las Vegas, with the goal of building
a honeypot that can lure in robocallers and allow technologists to
analyze how to block them in the future.
"Honeypots have been used extensively among information security specialists, but until today, there has been limited cross-pollination between their expertise and the efforts to fight telephone spam," said the agency.
"Unfortunately, the technical distinctions between a telephone call and an email have made it difficult to use internet security tactics in the battle against robocalls. We hope to change that by inspiring DEF CON experts to apply their knowledge and creativity on behalf of the millions of people frustrated by these illegal calls."
The contest is called "Zapping Rachel", as a tribute to the FTC's 2012 takedown of five robocalling operators who were sending out messages purporting to be from "Rachel in Cardholder Services." The amount of prize money hasn't yet been announced, but it's likely to be $50,000 based on past examples.
In 2012 the FTC offered the same sum to members of the public and small research teams who could come up with a way of blocking some robocalls. The agency ended up splitting the $50,000 prize pot between two winners, one of whom has since deployed a finished product that the FTC claims has since stymied four million robocalls.
The agency is now hoping that the talented men and women attending DEFCON can do better. The hacking conference, held August 7 to 10, immediately after the Black Hat briefings that cover more corporate hacking issues, is one of the oldest of its kind and attracts the cream of the hacking community – and whatever else floats to the top.
Such appeals from government agencies to hackers are nothing new. The NSA and others host recruitment booths at Black Hat, and last year the then-head of the NSA appealed directly to the hacking community for support. But at the same time, DEFCON banned federal staff from its floor, citing Snowden's leaks about NSA spying as the cause.
Nevertheless, if there's a sufficient purse up for grabs, the hacking community should be able to come up with some good ideas to help stop the robocalling industry from interrupting dinners across the land
"Honeypots have been used extensively among information security specialists, but until today, there has been limited cross-pollination between their expertise and the efforts to fight telephone spam," said the agency.
"Unfortunately, the technical distinctions between a telephone call and an email have made it difficult to use internet security tactics in the battle against robocalls. We hope to change that by inspiring DEF CON experts to apply their knowledge and creativity on behalf of the millions of people frustrated by these illegal calls."
The contest is called "Zapping Rachel", as a tribute to the FTC's 2012 takedown of five robocalling operators who were sending out messages purporting to be from "Rachel in Cardholder Services." The amount of prize money hasn't yet been announced, but it's likely to be $50,000 based on past examples.
In 2012 the FTC offered the same sum to members of the public and small research teams who could come up with a way of blocking some robocalls. The agency ended up splitting the $50,000 prize pot between two winners, one of whom has since deployed a finished product that the FTC claims has since stymied four million robocalls.
The agency is now hoping that the talented men and women attending DEFCON can do better. The hacking conference, held August 7 to 10, immediately after the Black Hat briefings that cover more corporate hacking issues, is one of the oldest of its kind and attracts the cream of the hacking community – and whatever else floats to the top.
Such appeals from government agencies to hackers are nothing new. The NSA and others host recruitment booths at Black Hat, and last year the then-head of the NSA appealed directly to the hacking community for support. But at the same time, DEFCON banned federal staff from its floor, citing Snowden's leaks about NSA spying as the cause.
Nevertheless, if there's a sufficient purse up for grabs, the hacking community should be able to come up with some good ideas to help stop the robocalling industry from interrupting dinners across the land
Subscribe to:
Comments (Atom)