It was the end of an era yesterday when the Internet's largest (and highly profitable) black market website Silk Road was finally taken down by the feds. Its proprietor Ross William Ulbricht (aka Dread Pirate Roberts) was taken into custody and now we're learning a lot about the site that offered everything from drugs to assassins. We're also learning about the limits of online anonymity.
Silk Road
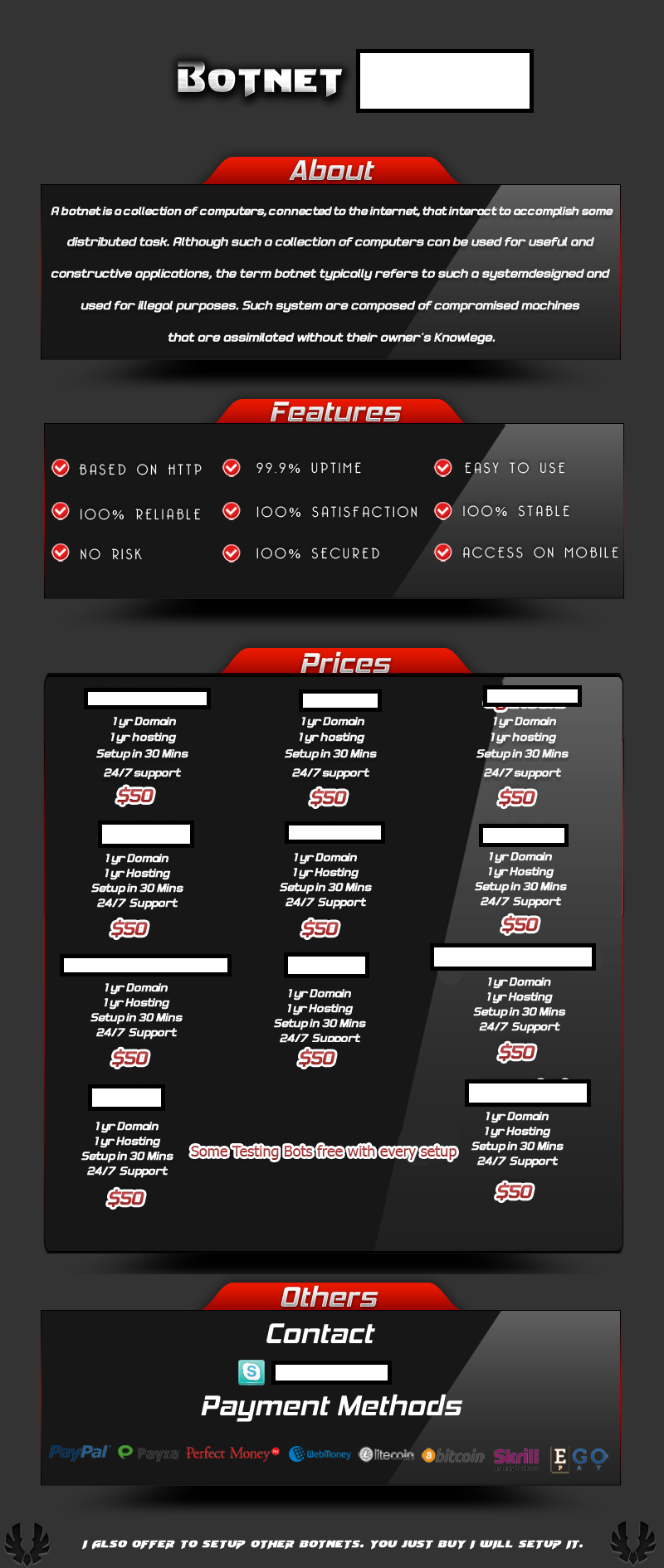
Named for the ancient cross-desert trade route, Silk Road was a marketplace designed to let users sell their wares—particularly, illegal goods and services. According to documents filed in conjunction with the investigation, the service saw billions of dollars pass through it in the form of untraceable Bitcoins.
To protect the site's users, Silk Road took advantage of the Tor (The Onion Router) anonymity network which bounces your request around to make it harder to track. When you connect to Silk Road, and other websites secured by Tor, your request is bounced through a series of volunteer servers. The request uses encrypted layers, like an onion, so that each relay server can only see where the request has immediately arrived from and where it will go next.
For instance, if you're on computer A trying to connect to website E, your request is bounced through Tor servers B, C, and D. Server B can see where you are because it's the first hop in the chain, but it doesn't know that you're trying to reach website E. Server D does know what website your request is headed to, but it doesn't know where you are. Server C doesn't know much of anything.
It's a clever system that has protected journalists and human rights activists, in addition to providing a modicum of security to less reputable operations. But like all security technology, it can be beaten.
Breaking Tor
Back when we looked at the Pirate Bay Browser, we highlighted a few of the problems with Tor. The big one, and the one that Tor has always admitted to, is that with careful traffic monitoring and a little math you can figure out who connects to what on Tor.
"The way we generally explain it is that Tor tries to protect against traffic analysis, where an attacker tries to learn whom to investigate," reads a 2009 blogpost from Tor. "But Tor can't protect against traffic confirmation (also known as end-to-end correlation), where an attacker tries to confirm a hypothesis by monitoring the right locations in the network and then doing the math."
Basically, if you think that person A is connecting to website E, you can sit at the entry to the Tor network and at an exit point, you can eventually infer the path of travel. But you have to know who to watch before you start your investigation.
Alternatively, you can be infected with malware while on a Tor site and have your computer's identifying information sent off to an observer. This is how the FBI was reportedly able to crack a notorious child pornography ring and bring charges against its operator, Eric Eoin Marques.
In that investigation, it appears that the FBI took control of Freedom Hosting—which hosted Marques's site—and used them to display an error message. Within the error message was an iFrame which in turn injected code onto the computer of anyone who visited a Freedom Hosting site. Wired writes that this code captured the infected computer's MAC address and Windows host name. This information was then packaged up and sent back to an unidentified server somewhere in Northern Virginia.
Plain Ol' Detective Work
In the case of Silk Road, the investigation appears to have relied on more traditional policework than breaking Tor. Wired reports that the feds simply looked around for the earliest mention of Silk Road on the Internet. That led to a posting on a magic mushroom forum, which in turn led to Ulbricht's Gmail account.
That's not the whole story, and in fact there are a lot of gaps in the chain of events. Police somehow got a hold of several fake IDs with Ulbricht's face on them during a border check, and somehow were able to trace Silk Road's servers. But the initial connection to Ulbricht appears to have required no special hacking, just some persistent Googling and subpoenas.
The lesson here is that behind all the encryption and obfuscation is a person. A person who makes mistakes, a person who leaves clues, and a person who is now facing serious charges. As long as people are still people, they'll always be vulnerable.