It is not often that we cover subject matter in a computer security blog that require a “
trigger warning”,
but today is one of those days. The following blog deals with
potentially difficult information regarding protecting people who have
been the victims of domestic abuse or stalking that could trigger an
extreme reaction in people who’ve been traumatized by similar
experiences.
_____
Domestic violence is not something that gets discussed much in
information security circles, for a variety of possible reasons, but
there are few people that need advice on assuring their online safety
more urgently than victims of stalking and domestic abuse. How exactly
do the particular information security needs of people in these
situations differ from the norm? What can people do to protect
themselves when there is a known and persistent threat? After looking
into this, I am left with as many questions as answers.
Before we get into the meat of this article, let me provide a frame
of reference: I will be focusing on those victims of domestic abuse and
stalking that have escaped the situation, and are now looking to avoid
further contact with their abusers. The subtleties of getting protection
while still in the environment in which domestic abuse is taking place
go more into the realm of psychology than simple computer security
concerns. And because there is so much more to be explored on this
particular subject, think of this article less as something
prescriptive, and more of an open-ended discussion. If you have
experience on this subject, I welcome you to add your voice to the
comments to help educate me as well as other readers.
Digital Privacy
Before discussing specific security recommendations, it’s important
to point out that any computing devices (that is to say, both laptops
and desktops as well as phones and tablets) that predate exiting the
domestic violence situation should be considered compromised, and should
ideally be replaced, or at least restored to factory default if at all
possible. This will decrease the possibility of spyware or other
tracking software being present on the device. You may wish to back up
(and encrypt) your data to an external hard drive or remote location
first.
It is obvious that all those things that security advocates are wont
to say to help people protect their data applies far more acutely to
those who are trying to hide themselves from a determined and
potentially violent individual. Let us quickly cover those security
basics that are even more essential to victims of abuse:
- Regularly updated software
Most Spyware installations now exploit vulnerabilities in software to
install more silently, but you can help combat this by updating
and patching your operating system and any applications on your computer
as soon as possible. The latest versions of the major operating systems
are set by default to at least alert you to both application and OS
updates. And over time, operating systems are including more and more
security features to help alert you to and/or combat attacks.
- Network and on-disk encryption
The best way to protect your data from prying eyes is to make more of it
unreadable to outside parties. And the best way to do this is to encrypt as much as you can both data that is saved on your hard disk, and data that you send out of your machine, via email, web or other methods. There are tools to help you encrypt email, and to ensure more of your web sessions are encrypted. There are also chat clients that allow you to exchange encrypted messages with your contacts. You can use a VPN client to give yourself an additional layer of security. And many of these things are available for free or low cost.
- A comprehensive security suite
Spyware is easily found or purchased online, which will allow an
attacker to view keystrokes, web-surfing history, and potentially to
eavesdrop on audio or video capabilities on a victim’s computer. A
reputable anti-malware product is a good idea, but it would also be
advisable to have at least a software or hardware firewall as well,
regardless of what operating system you use. You may also wish to look
into supplementing your security suite with an application whitelist as well, which limits allowed applications to a specific list of approved software.
- Good password hygiene
Most of our online life revolves around logging in to various sites and
services. It is also one of the most easily breached parts of our
digital identity. Whether you use a password manager or come up with a
system to create a strong, memorable and unique password for each of your various online accounts, be sure to change those passwords regularly.
Everyday activities are fraught
Whether an intruder’s motivation is financial or personal – as in the
case of domestic abuse – anyone looking to gain another’s data has two
main ways to go about it: by force, or by social engineering. Gaining
data by force would include approaches like direct attacks (either
physical or digital), such as the use of malware or hacking into online
accounts. Social engineering is a term sometimes applied to any way an
attacker can convince someone to give them access to data. The target
may be either the victim himself or herself, or a third party.
The advice given above is primarily intended to protect against
direct attacks like malware, and hacking, and to a lesser extent
phishing. Technology and good common sense will not necessarily protect
you against every sort of direct attack, but it can lessen the risk
considerably or at least make it far more difficult and time-consuming
for the attacker.
However, not all our data is within our control, and this is where
things can get very problematic and complicated. We are all required to
provide a variety of personal information in our day-to-day lives –
everywhere from the car service center to the accountant. Unfortunately,
once the data is out of our hands, it is also out of our control. Many
companies have data retention policies and are strict about giving out
customers’ information, but many other places do not. Fortunately, the
places where it is most important to keep your contact information up to
date are also the ones that are most likely to have strict policies.
This is where there are more questions than answers. There is plenty
of advice out there for people who are trying to protect themselves
after a domestic violence incident. The variety of tips and techniques
are seemingly endless, but they boil down to a few basic ideas:
- Relocate
Put physical distance between yourself and your abuser. If you
move to another state, make sure your restraining order covers this
situation. Be aware that different countries may have different
laws regarding domestic violence, or restraining/protection orders. In
some instances you may be able to pursue protection orders that cross
national borders, depending on the countries in question.
- In the US, apply to the address confidentiality program in your state
Programs exist to allow people who have been victims of certain types
of crimes to have a confidential mailing address, separate from their
physical address. Check this list of address confidentiality programs in the US to see if you are eligible.
- Open a post office box to receive mail
Ideally, you should have a place to receive mail and use for
certain accounts and services, which is not your home address. Be aware
that this is not useful for all services, especially those that require
your home address, such as certain types of insurance.
- Close accounts that you both have access to
Regardless of how innocuous the account access might seem, if a
joint account contains any personal information or historical activity,
this could be used by an abuser for social engineering purposes. It is
best to close existing accounts and start with no history from previous
accounts. This applies equally to accounts like phone service or store
loyalty programs or digital accounts such as email or social networking
sites.
- Be aware of location-tracking
If you open new accounts on various services, be aware that many social
media sites actively share your location, or it may be leaked when you
“check in” to a physical location, or share a photo with
GPS location data embedded in it. Set the privacy options for any
services you use to their highest settings, and disable the storing GPS
location data in pictures. Also, carefully consider the levels of risk
associated with using online services: It may be safer to stay offline.
- Be aware of your surroundings, both physically and digitally
As you go about your daily routines, both in the physical world and
the digital one, it is important to be aware and mindful of your
surroundings. What information are you intentionally giving out?
What information are you (or others, on your behalf) inadvertently
giving out or leaving lying around? Who can see where you are,
where you are going, or where you have been?
- Guard your data
Once you are aware of what data you have to be gleaned, take steps to
keep it protected while it is in your care (such as with encryption, or
being judicious with app permissions) and be cautious about who you
give information out to. Whenever possible, give out only information
that does not link to your home address.
- Avoid web sites and services administered or moderated by the abuser
If your abuser regularly accesses (or even helps administrate or
moderate) a web site you both use, stop accessing it, as they may have
access to server logs which contain your network connection’s IP
address. IP addresses can be geo-located in order to determine
approximately where a computer is located. This also includes online
games, as in-game communications and actions may reveal your location as
well.
- Block all contact from the abuser
Email and messaging account traffic can similarly be used by an abuser
to gather location data on their victim, so wherever possible block
accounts known to be used by him or her. You may also wish to block
accounts used by friends or family of the abuser.
The advice here is solid in theory, but in practice things can be
significantly more difficult. Keeping this in mind, you may be able to
be proactive against some of the hurdles you may face. Having legal
paperwork including your restraining or protection order may make it
easier to get hefty fees or objections waived when you try to cancel
accounts or withhold certain information.
And other well-meaning people may undo your efforts to keep your
information private, if they are not aware of your situation. In a case
in Sweden, a woman and her two children left their abuser, but the
abuser
posted a plea on Facebook
and asked people to share his request to help him find his children,
resulting in the protected identities of the mother and children being
blown. As we often advise in security circles, no protection is 100%
secure. But the more ways you manage to cover your risks, the more time
and space you can gain to allow you to resurrect damaged defenses.
Additional Protection
There are additional steps you can take if you are looking for a more
thorough change of identity, though be aware that these changes will
not give you a completely clean slate, one that is unattached to your
old identity. The National Network to End Domestic Violence website
debunks some of the myths surrounding the process of changing your name and social security number.
You may also wish to try to remove as much of your presence from the
Internet as possible. While it is not entirely feasible to completely
remove your digital presence, you can certainly reduce it. This Gizmodo
article
lays out instructions for removing your presence from some of the more popular social networks.
Some final thoughts
The more real and physical the possible danger against which we are
recommending protection, the more scary it is as a writer to provide a
list that could potentially be (or in this case
necessarily is)
incomplete. This article barely scratches the surface of things to
consider. Due to the huge volume of legal requirements and permutations,
there are an almost infinite number of things you can (and potentially
should) do to protect yourself from an abuser. Ideally this is something
you should discuss with a lawyer or a social worker, so that you can
thoroughly cover ways to keep yourself safe.
Here are some additional resources, should you wish for further information on the subject:
- http://www.staysafeonline.org/data-privacy-day/privacy-and-domestic-violence/
- http://www.surviving-domestic-violence.com/
- http://epic.org/privacy/dv/
- http://www.nnedv.org/internetsafety.html
- http://www.mincava.umn.edu/categories/888
 Let’s discuss the (business) interaction that most commonly takes
place between a buyer and seller of such type of services. On the
majority of occasions, thanks to the fact that the vendor seeks to
efficiently supply what the market demands, basic OPSEC rules, ones
sometimes visible in Russian/Eastern European providers, are ignored.
For instance, the service we’re discussing in this post not only has its
site publicly searchable, it also features a YouTube advertisement.
Combined with the fact that it’s also soliciting customer inquiries
through a GMail account — no public PGP key offered — results in a
situation where a potential customer would think twice before contacting
the vendor. Moreover, these (international) underground market
propositions usually tend to acquire less technically sophisticated
customers who’d often seek their assistance in taking down a gaming
server, or not surprisingly, launch a Denial of Service attack against a
“friend’s” Internet connection. In comparison, the Russian/Eastern
European vendors would usually prefer to stay beneath the radar, and
will vet potential customers based on multiple factors — that includes
the actual target — before launching an attack on their behalf.
Let’s discuss the (business) interaction that most commonly takes
place between a buyer and seller of such type of services. On the
majority of occasions, thanks to the fact that the vendor seeks to
efficiently supply what the market demands, basic OPSEC rules, ones
sometimes visible in Russian/Eastern European providers, are ignored.
For instance, the service we’re discussing in this post not only has its
site publicly searchable, it also features a YouTube advertisement.
Combined with the fact that it’s also soliciting customer inquiries
through a GMail account — no public PGP key offered — results in a
situation where a potential customer would think twice before contacting
the vendor. Moreover, these (international) underground market
propositions usually tend to acquire less technically sophisticated
customers who’d often seek their assistance in taking down a gaming
server, or not surprisingly, launch a Denial of Service attack against a
“friend’s” Internet connection. In comparison, the Russian/Eastern
European vendors would usually prefer to stay beneath the radar, and
will vet potential customers based on multiple factors — that includes
the actual target — before launching an attack on their behalf.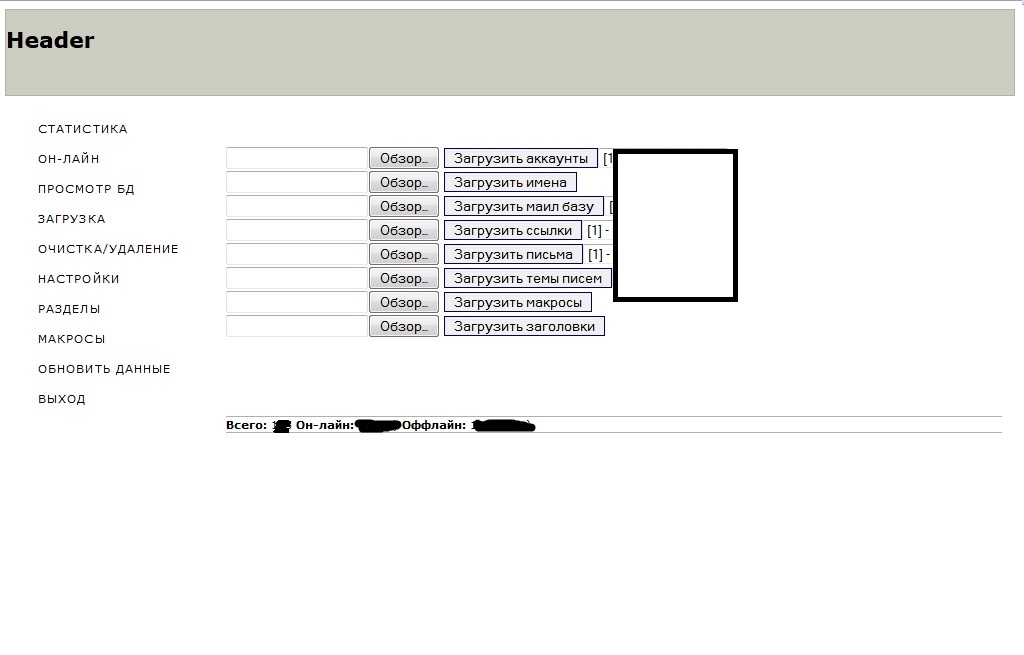
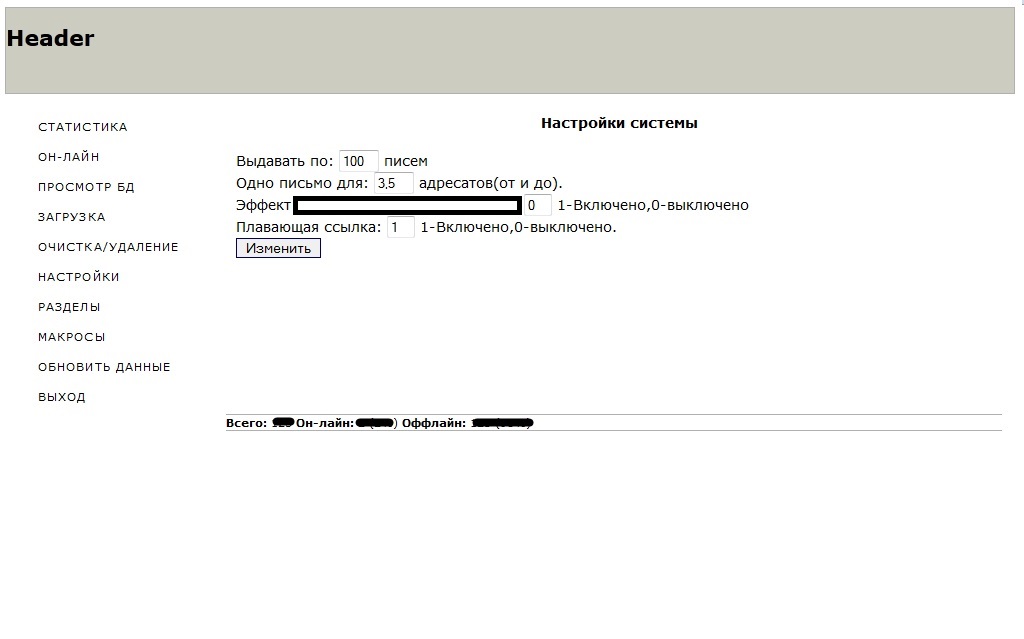
 According to the seller of this spam bot, the actual binary is around
56kb in size, and the C&C is PHP/MySQL based. The seller also
offers his personal advice, which is to consider relying on
According to the seller of this spam bot, the actual binary is around
56kb in size, and the C&C is PHP/MySQL based. The seller also
offers his personal advice, which is to consider relying on