Configured For Attack
The attack Amit used on my device has been covered already on his company's blog, but that didn't make it any less unnerving. It started with a large, friendly button on a website. I tapped it, the view immediate jumpt to the iPhone's Settings application where I was prompted to install a new configuration profile.
I'll pause right here to say that config profiles are useful for changing VPN settings, email settings, and so on for a large number of devices.That said, there's probably no need for the average user to install one. Though I was complicit in the installation, Amit pointed out that most users could be convinced to do the same with a little social engineering; perhaps by offering free video streaming or free Wi-Fi.
Once installed, Amit could see everything I typed on his screen. He could also force my web browser to visit different websites (in this case, the relatively benign Bing). Then, he politely asked if he could access the Facebook app on my phone. I said yes and, unbidden, the app launched on my screen. The next part was really scary: Amit was then able to login to Facebook in a browser, on his computer as me.
Amit said that if he were an attacker, he could now learn a lot about me and even impersonate me. Gaining access to social media and email is a critical step for attackers to spread malware or initiate scams because people inherently trust these systems.
He said that in some ways, the same was true for iOS. Referring to Apple's walled garden approach, Amit said, "in this case, perfection is bad for security because people trust everything they're doing." Most people, he argued, probably wouldn't think twice about installing a config profile because they trust their iOS devices so much.
I asked him if he'd seen this kind of attack in the wild. "We see it happening," he said, calling it the worst problem facing iOS device today.
Skycure's Solution
Before he completely scared the pants off me, Amit explained what the new software from Skycure actually does to keep you safe. On Android, most security applications simply scan apps to check for malware. Skycure, on the other hand, keeps tabs on network traffic, looking for potentially malicious communications.
There's a whole business IT end to their service, but the most interesting part is on the phone. Instead of watching your actual network traffic, they use a "honey pot" approach which mimics the traffic of applications like Mail. If it detects anything untoward, it secures your communications with VPN—or other remediation tactics. And, thankfully, it can remove nasty config profiles.
Amit explained that their dynamic approach means that your Internet connection won't always be throttled by VPN, and your battery won't be unnecessarily taxed either. Also, it lets your communications stay private by mimicking network traffic, instead of monitoring it. They also crowdsourced data on attacks, so that they could identify infected networks or geographic areas (like airports) that attackers frequently use.
Skycure is targeted at businesses, which means I won't be reviewing it any time soon. But it sounds like a remarkably smart way to lock down threats on the iOS platform. Hopefully we'll be seeing this kind of protection come down to the consumer level.
Stay Safe
If you're worried that you might have installed a config profile in the past (I was surprised to find one that I couldn't identify), it's easy to check. Open the Settings app, tap General, and then scroll all the way down. At the bottom you should see a block of three options above Reset: iTunes Wi-Fi Sync, VPN, and Profile.
Don't see Profile? Great news: you don't have any configuration profiles installed on your device. If you do see the page, open it up and try to remember what these are for. If any of them seem suspicious, you can easily delete them by tapping the big red Remove button.
Of course, the best way to avoid this attack is to simply not install configuration profiles from anyone you don't really trust. Or at all. If you ever see a website asking to install one on your device, don't do it!
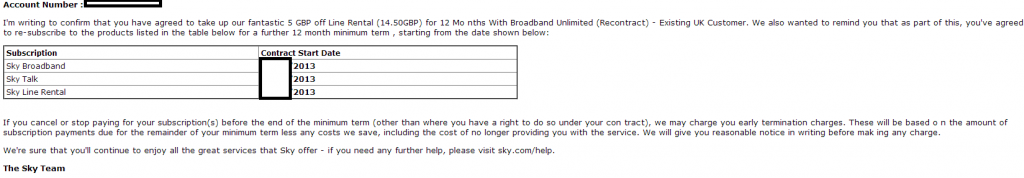 Detection rate for the Sky themed sample:
Detection rate for the Sky themed sample: