The super worm known as Stuxnet was but a cog in an active US war
program in which hundreds of thousands of network implants and backdoors
in Iran networks were actively maintained to facilitate a devastating
barrage of hacking attacks, a documentary claims.
Zero Days, due to screen at the Berlin Film
Festival today, claims that Stuxnet was just one part of an operation
called "Olympic Games" that is itself part of a wider effort dubbed
"Nitro Zeus" that involves hundreds of US defence personnel.
Nitro Zeus may also involve Israel, the film alleges.
Reports from those who've seen or been briefed on the
film suggest it alleges that Stuxnet's authors attempted to keep the
program covert by restricting the malware to infect only Iranian
machines.
Forte Mead hackers worked furiously to mop-up infected computers after a leak became apparent.
Israeli counterparts reportedly screwed the pooch
when they later unleashed a more aggressive and noisier version of
Stuxnet that infected thousands of computers across more than 115
countries.
The worm was soon discovered in 2010 and promptly analysed - and gaped at askance - by the security industry and media.
The film asserts that Stuxnet contained four zero day
vulnerabilities and was precision-designed for the Natanz facility
using intelligence supplied by Britain's GCHQ.
It is not stated in the documentary whether the GCHQ
had knowledge of Nitro Zeus, a fact that could breach national laws
regarding use of intelligence material in that country.
US State Department and National Security Agency
officials expressed concern over the likelihood that Nitro Zeus would
devastate civilian infrastructure.
One unnamed source said Nitro Zeus planners had "no f**king clue" regarding the potential impacts of the attacks.
Former CIA and NSA director Michael Hayden says while
he had no knowledge of Nitro Zeus the program has prematurely
legitimised state-backed network centric warfare before rules of
engagement could be agreed.
Information Security, Ethical Hacking, website Security, Database Security, IT Audit and Compliance, Security news, Programming, Linux and Security.
Thursday, 18 February 2016
Tim Cook says Apple will fight US gov’t over court-ordered iPhone backdoor
Late yesterday, a federal judge in California ordered Apple to help the US government (the FBI) unlock and decrypt the iPhone 5C belonging to Syed Rizwan Farook, who shot up an office party in San Bernardino in December 2015.
In the past, Apple has helped extract data from iPhones when issued with an appropriate warrant. Since iOS 8, however, full encryption has been enabled by default—a move that was seemingly introduced specifically to prevent such data-grabs by governments. "Unlike our competitors, Apple cannot bypass your passcode and therefore cannot access this data," the company wrote on its website at the time. "So it's not technically feasible for us to respond to government warrants for the extraction of this data from devices in their possession running iOS 8."
Now, however, Judge Sheri Pym has ordered Apple to introduce a backdoor to help the FBI unlock the iPhone—and, unsurprisingly, Tim Cook is not best pleased.
Cook's "message to our customers" is quite impressively aggressive. It begins by explaining why we need encryption, moves onto a brief history of the San Bernardino case, and then explains exactly what the FBI actually wants from Apple. Here's the core of the letter:
We have great respect for the professionals at the FBI, and we believe their intentions are good. Up to this point, we have done everything that is both within our power and within the law to help them. But now the U.S. government has asked us for something we simply do not have, and something we consider too dangerous to create. They have asked us to build a backdoor to the iPhone.From the court order, we even know what kind of backdoor the US government wants:
Specifically, the FBI wants us to make a new version of the iPhone operating system, circumventing several important security features, and install it on an iPhone recovered during the investigation. In the wrong hands, this software — which does not exist today — would have the potential to unlock any iPhone in someone’s physical possession.
The FBI may use different words to describe this tool, but make no mistake: Building a version of iOS that bypasses security in this way would undeniably create a backdoor. And while the government may argue that its use would be limited to this case, there is no way to guarantee such control.
Apple's reasonable technical assistance shall accomplish the following three important functions: (1) it will bypass or disable the auto-erase function whether or not it has been enabled; (2) it will enable the FBI to submit passcodes to the SUBJECT DEVICE for testing electronically via the physical device port, Bluetooth, Wi-Fi, or other protocol available on the SUBJECT and (3) it will ensure that when the FBI submits passcodes to the SUBJECT DEVICE, software running on the device will not purposefully introduce any additional delay between passcode attempts beyond what is incurred by Apple hardware.Basically, right now there are measures in place to stop someone from picking up your iPhone and brute-forcing the code to unlock your phone. The FBI wants a backdoor that allows such a brute-force attack to take place. With direct passcode input through the iPhone's Lightning port, and no additional delay between passcode attempts, cracking the code would be very easy.
Apple, for its part, opposes the court order. "We can find no precedent for an American company being forced to expose its customers to a greater risk of attack," Cook writes. "We are challenging the FBI’s demands with the deepest respect for American democracy and a love of our country ... While we believe the FBI’s intentions are good, it would be wrong for the government to force us to build a backdoor into our products."
Finally, one last thought: Tim Cook published the open letter at midnight Pacific time, when most Americans were already asleep. Europe, however, was just waking up—and Europeans tend to get quite upset by egregious breaches of privacy. If Apple was compelled to introduce such a backdoor for the FBI, European governments would have access to it as well.
Israeli military techies cook up security alerts software
Lessons from building the threat intelligence platform for the
Israeli Defence Force form the technical foundations of a new security
startup called Siemplify.
Siemplify’s tech is designed to contextualise threat alerts from the disparate array of security technologies on enterprise networks (anti-malware, intrusion detection systems, firewalls and more). Its platform acts as a central hub linking an organisation’s existing security, threat intelligence and risk management tools, including Splunk and other popular (security information and event management systems) SIEMs, before consolidating and correlating alerts.
Visualisation and modelling tools are then used to present prioritised threat information as visual story lines, helping analysts to identify the root causes of security problems. The security operations platform is positioned as a means for banks, large enterprises and governments to identify and resolve malware and hacker attacks far more quickly.
Amos Stern, Siemplify chief exec, led the cybersecurity department in charge of building the threat investigation platform for the Israel Defence Forces. Stern served in the IDF for nine years between 2003 to 2012 before working in the private sector for three years, working on sales and business development with Elbit Systems. Other senior execs also come from the same background in the IDF, which began producing security startup hits beginning with Check Point back in the '80s, back when Stock Aitken and Waterman were churning out hit records.
Siemplify is seeking to apply methodologies gained from military intelligence - such as real-time graph analysis, machine learning and Big Data - to cybersecurity. Incidents are prioritised according to a threat score by the platform, which provides triage, ticketing and case management functionality.
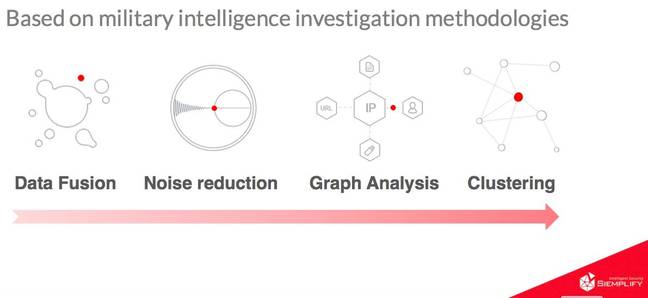 Military intelligence techniques applied to sort security alerts
Military intelligence techniques applied to sort security alerts
Military systems are not dramatically different from
enterprise systems but they do tend to be a few steps ahead, according
to Stern. For example, virtualisation technology was standard in the IDF
as long ago as 2005. Militaries tends to be early adopters of “bleeding
edge” new tech while enterprises are more conservative, according to
Stern, who added that the gap was nonetheless closing.
Stern built threat investigation systems as well as leading on emergency cyberthreat response while serving with the IDF in what he describes as a defensive capacity. Stern told El Reg that many of the problems enterprises face have already been solved in the arena of military intelligence.
“The problem is not detection per se but discerning the threats hidden in the noise of thousands of alerts generated by the disparate security monitoring systems,” Stern explained. “This makes it impossible to see the broader attack chain and identify root cause quickly.”
The Siemplify Threat Analysis Platform is designed to automatically correlates security alerts, identifies and prioritises incidents, before graphically depicting the complete threat chain. Conventional SIEM collect alerts but lack the ability to add context that Siemplify offers, according to Stern. Big Data analytics built into Siemplify “empower analysts”, according to Stern.
“You need noise reduction because you are generating a lot of alerts,” Stern told El Reg. “Some of the banks we’ve worked with have 50 different controls that create many different silos.”
“Siemplify can aggregate and prioritise information, as well as providing a timeline,” he added.
Stern told El Reg: “Intel analysts using this platform don’t need to be technical. For example they wouldn’t need to write or program a query.”
Investors affiliated to Intel, Red Hat, Rackspace and others have put $4m into the startup. Early adopters include some of Israel’s largest banks, telecom and pharmaceutical firms. Pilots are under way at Fortune 50 companies in consumer packaged goods and financial services, said the founders
Siemplify’s tech is designed to contextualise threat alerts from the disparate array of security technologies on enterprise networks (anti-malware, intrusion detection systems, firewalls and more). Its platform acts as a central hub linking an organisation’s existing security, threat intelligence and risk management tools, including Splunk and other popular (security information and event management systems) SIEMs, before consolidating and correlating alerts.
Visualisation and modelling tools are then used to present prioritised threat information as visual story lines, helping analysts to identify the root causes of security problems. The security operations platform is positioned as a means for banks, large enterprises and governments to identify and resolve malware and hacker attacks far more quickly.
Amos Stern, Siemplify chief exec, led the cybersecurity department in charge of building the threat investigation platform for the Israel Defence Forces. Stern served in the IDF for nine years between 2003 to 2012 before working in the private sector for three years, working on sales and business development with Elbit Systems. Other senior execs also come from the same background in the IDF, which began producing security startup hits beginning with Check Point back in the '80s, back when Stock Aitken and Waterman were churning out hit records.
Siemplify is seeking to apply methodologies gained from military intelligence - such as real-time graph analysis, machine learning and Big Data - to cybersecurity. Incidents are prioritised according to a threat score by the platform, which provides triage, ticketing and case management functionality.
 Military intelligence techniques applied to sort security alerts
Military intelligence techniques applied to sort security alertsStern built threat investigation systems as well as leading on emergency cyberthreat response while serving with the IDF in what he describes as a defensive capacity. Stern told El Reg that many of the problems enterprises face have already been solved in the arena of military intelligence.
“The problem is not detection per se but discerning the threats hidden in the noise of thousands of alerts generated by the disparate security monitoring systems,” Stern explained. “This makes it impossible to see the broader attack chain and identify root cause quickly.”
The Siemplify Threat Analysis Platform is designed to automatically correlates security alerts, identifies and prioritises incidents, before graphically depicting the complete threat chain. Conventional SIEM collect alerts but lack the ability to add context that Siemplify offers, according to Stern. Big Data analytics built into Siemplify “empower analysts”, according to Stern.
“You need noise reduction because you are generating a lot of alerts,” Stern told El Reg. “Some of the banks we’ve worked with have 50 different controls that create many different silos.”
“Siemplify can aggregate and prioritise information, as well as providing a timeline,” he added.
Stern told El Reg: “Intel analysts using this platform don’t need to be technical. For example they wouldn’t need to write or program a query.”
Investors affiliated to Intel, Red Hat, Rackspace and others have put $4m into the startup. Early adopters include some of Israel’s largest banks, telecom and pharmaceutical firms. Pilots are under way at Fortune 50 companies in consumer packaged goods and financial services, said the founders
Subscribe to:
Comments (Atom)