In this post, I’ll discuss a managed botnet setup as a service, targeting novice cybercriminals who are looking for remote assistance in the process of setting up the C&C infrastructure for their most recently purchased DIY botnet generation tool. I’ll also discuss the relevance of these services in the content of the (sophisticated) competition, that’s been in business for years, possessing the necessary know-how to keep a customer’s fraudulent/malicious campaign up and running.
Sample screenshot of the (international) underground market proposition:
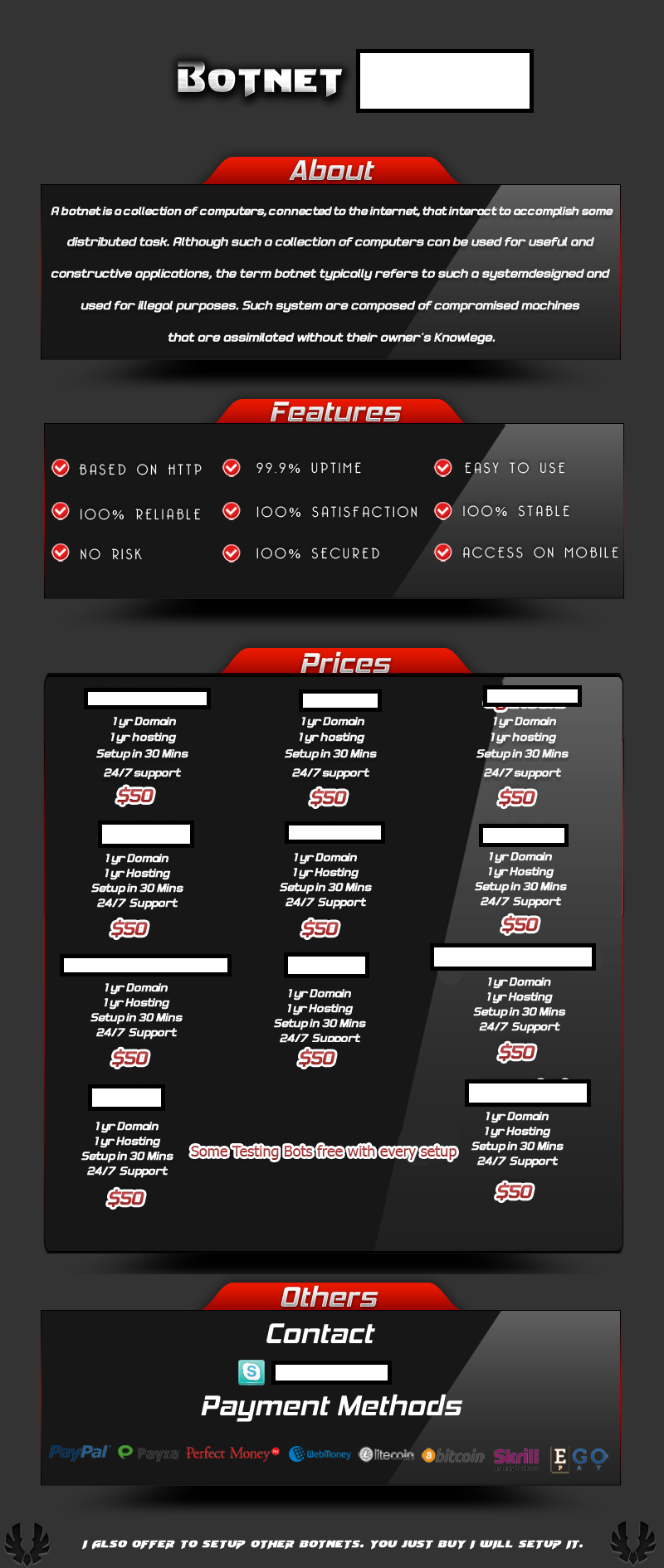 For the static amount of $50, the cybercriminal behind the managed
botnet setup service will configure, register HTTP based C&C
domains, as well as host them for one year, and currently supports 11
different DIY malware/botnet generating tools. The service’s value
proposition is similar to that of a recently profiled managed bulletproof hosting service for malicious Java applets,
in terms of lacking the necessary know-how and experience to ensure
smooth (cybercriminal) operations. Does a cybercriminal need to take
advantage of one of the market leading (Russian) bulletproof
cybercrime-friendly services in order to increase the life cycle of his
campaigns? Not necessarily, as the botnet generating tools offered by
this service can be best described as ‘beneath the radar‘ botnets, that is, small botnets that rarely make the news headlines.
For the static amount of $50, the cybercriminal behind the managed
botnet setup service will configure, register HTTP based C&C
domains, as well as host them for one year, and currently supports 11
different DIY malware/botnet generating tools. The service’s value
proposition is similar to that of a recently profiled managed bulletproof hosting service for malicious Java applets,
in terms of lacking the necessary know-how and experience to ensure
smooth (cybercriminal) operations. Does a cybercriminal need to take
advantage of one of the market leading (Russian) bulletproof
cybercrime-friendly services in order to increase the life cycle of his
campaigns? Not necessarily, as the botnet generating tools offered by
this service can be best described as ‘beneath the radar‘ botnets, that is, small botnets that rarely make the news headlines.We expect to continue observing similar (international) underground marketplace propositions, with more cybercriminals realizing the market segment potential for products and services targeting novice cybercriminals exclusively.
No comments:
Post a Comment