Tracking users’ location through their Wi-Fi network is not something
new however it should be disabled. Here’s a simple image guide on
disabling your location tracking on Windows 10 phone.
This used to happen because whenever the device was disconnected from
a WiFi network, it continues to try to connect to any nearby accessible
wireless network.
Microsoft has equipped its Windows 10
mobile phone with numerous new features and the security aspect has
also been tweaked a little. In its previous versions, the phone offered
reasonable security since at places like shopping malls, public areas
and supermarkets your movement could be tracked if the device was
connected to a WiFi hotspot.
Once the phone finds the connection, the MAC address logs into the wireless network and this information can be used by third parties for tracking your movements whenever you enter the area.
Since large venues have multiple wireless routers, the chances of tracking your location become brighter.
Windows 10, however, offer enhanced privacy on Lumia 950 and Lumia 95- XL through the Random Hardware Access feature.
It randomly generates hardware addresses to make it difficult for third parties to track your mobile phone’s location if it gets connected to a nearby wireless network.
However, this feature is not activated by default on these phones. Therefore, we are providing you the necessary guidelines to enable Random Hardware Addresses to feature in your Win 10 mobile phone.
Open the Start screen and bring All Apps by swiping left.
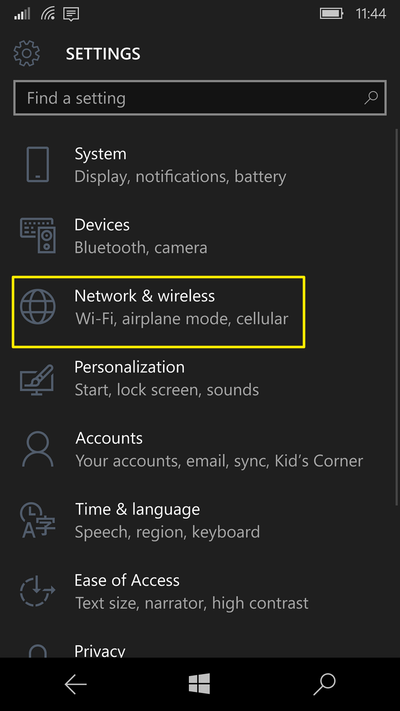
Now locate and open the Settings app and select Network and Wireless and then Wi-Fi.
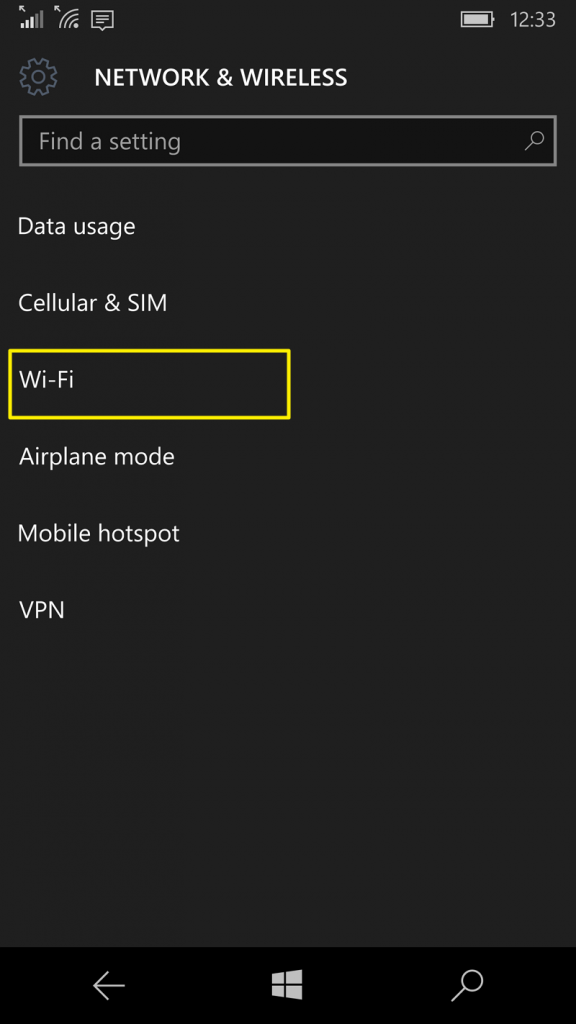
Now find the Manage button by scrolling down.
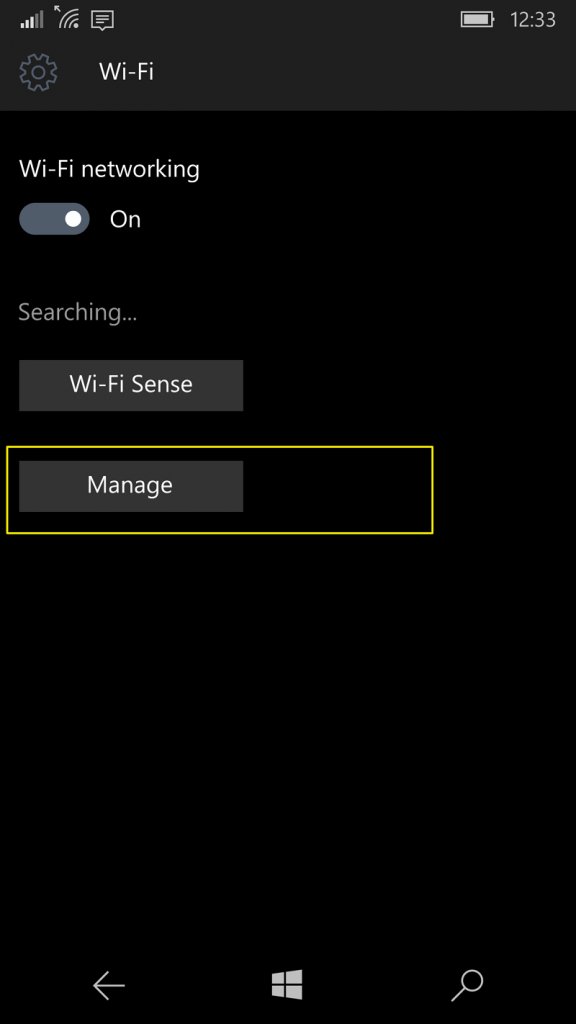
Once there, ensure to toggle the Use random hardware addresses option to On position and the feature will be enabled.
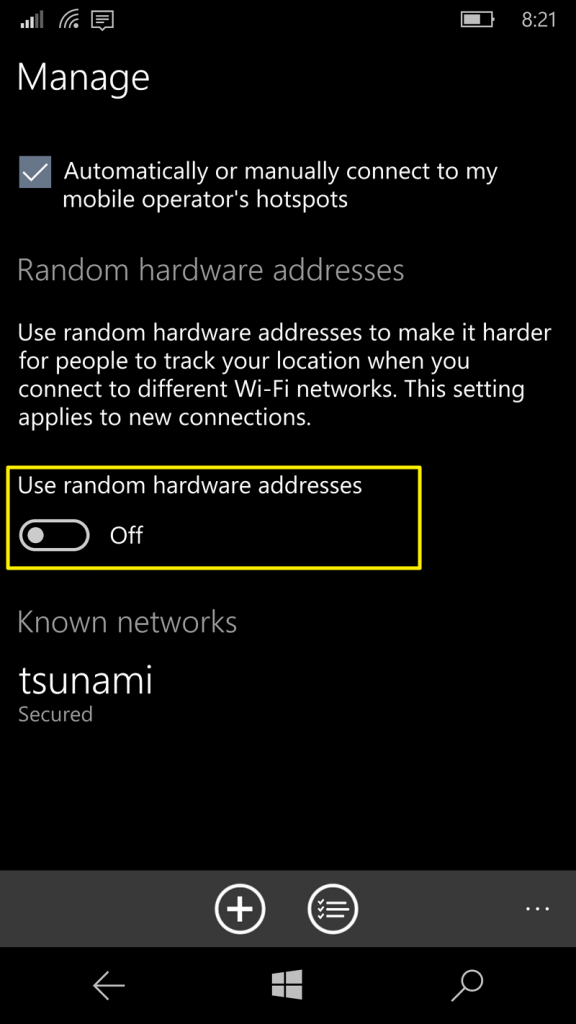
Activate Random Hardware addresses on specific WiFi networks.
You may also opt to use this feature on specific networks.
Select Wi-Fi option.

Select the network that you need to prevent from location tracking and by scrolling down select any one of the following options:
On
Off
Change Daily
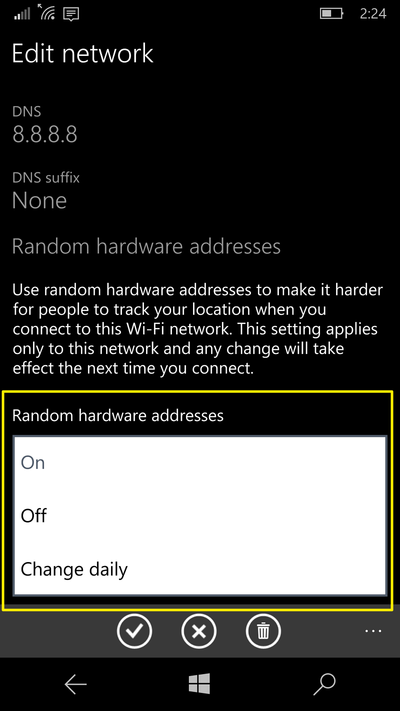
After selecting the option, return to Wi-Fi and by holding the wireless network you are currently connected to and tap on Delete option.
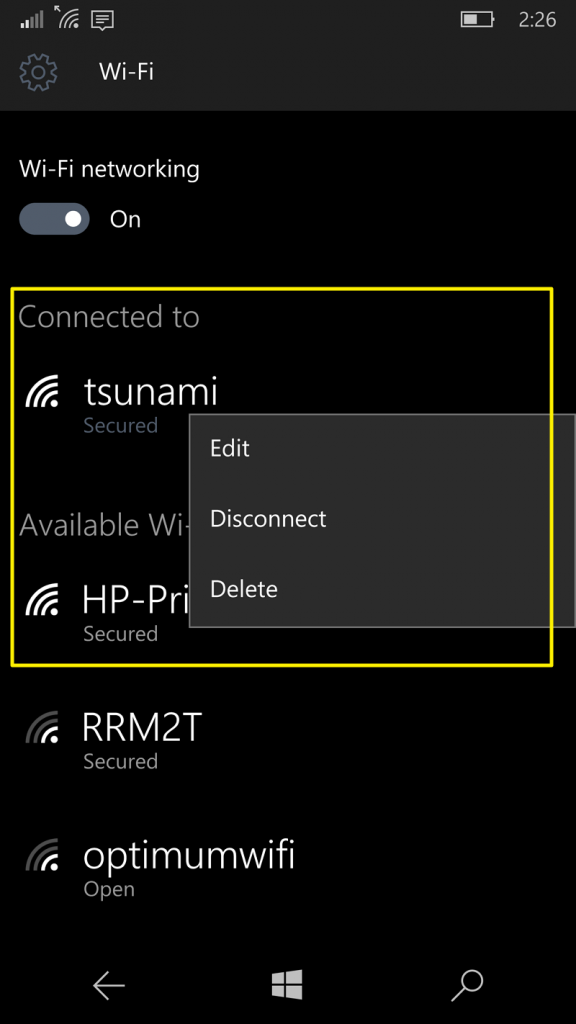
Reconnect your device to the same wireless network so that the new settings could be enabled.
Another feature of random MAC addresses is that it also hides your device name as it tries to connect to a wi-fi network using random hardware address as the name.
Remember that this feature is not particularly important to be enabled at home or office because at some areas device tracking is important to keep the network secure and in compliance with the policies of the company you work for.