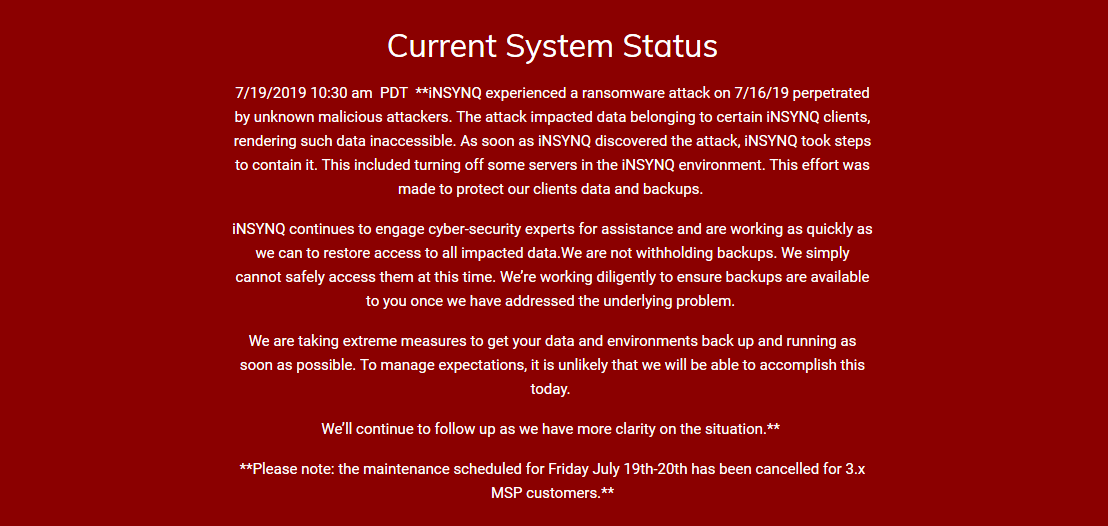
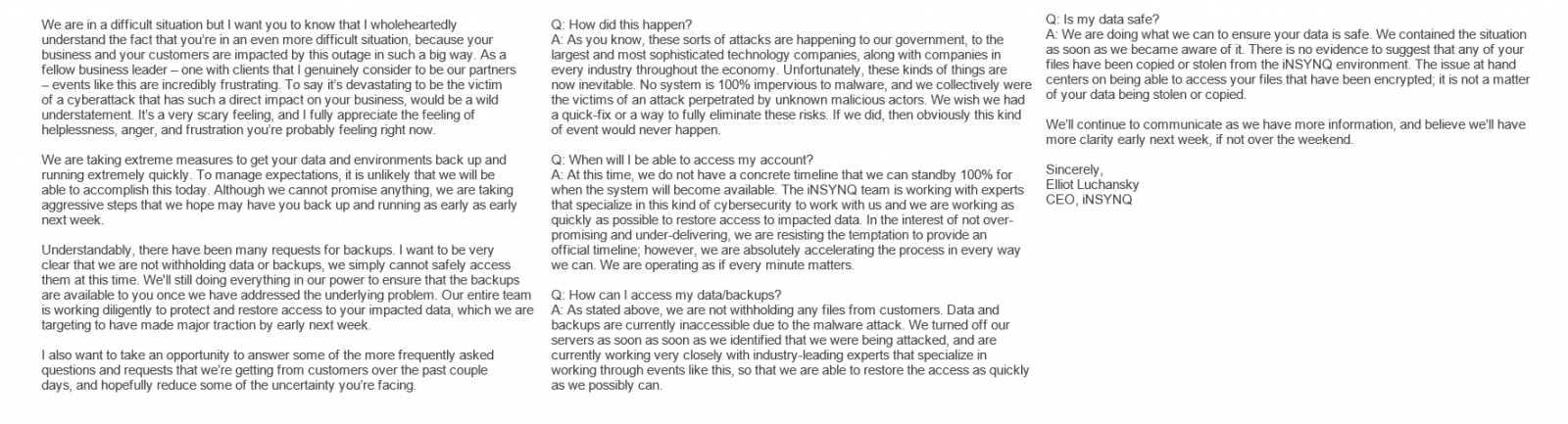
A computer virus which has hit City Power has resulted in a blackout to its internet technology system, leaving scores of Johannesburg residents unable to purchase electricity, as their kilowatts approach 0.00.
The power utility’s spokesperson Isaac Mangena said the virus had attacked its database and other software, impacting on most of its applications and networks.
The virus has also prevented those who had already bought their electricity from uploading it to their meter boxes.
The City Power website is also affected by the virus.
"It may also affect our response to some outages, as the system to order and dispatch material is affected. City Power IT team has been working since early morning 01:00 to fix this problem," Mangena said.
He said they hoped to have the glitch fixed by midday on Thursday.
On Wednesday, the utility announced that it was experiencing capacity constraints due to the cold weather in Johannesburg.
Mangena said cold weather conditions could result in unplanned outages, as the electrical system experienced overloading when demand increased.
He said plans were in place to deal with unplanned outages. The key focus of the plan was to attend to those areas that experienced repeated unplanned outages on the same day or week, he said.
"We have also increased the number of technicians in areas that are prone to repeated unplanned power outages.
"More teams have been put on standby so that they can be dispatched to attend to outages and respond to emergency calls," he said.
Residents have been urged to use electricity sparingly during this time.