Throughout the years, cybercriminals have been perfecting the process of automatically abusing Web application vulnerabilities to achieve their fraudulent and malicious objectives. From the utilization of botnets and search engines to perform active reconnaissance, the general availability of DIY mass SQL injecting tools as well as proprietary malicious script injecting exploitation platforms, the results have been evident ever since in the form of tens of thousands of affected Web sites on a daily basis.
We’ve recently spotted a publicly released, early stage Python source code for a Bing based SQL injection scanner based on Bing “dorks”. What’s the potential of this tool to cause any widespread damage? Let’s find out.
Sample screenshots of the Python script in action:
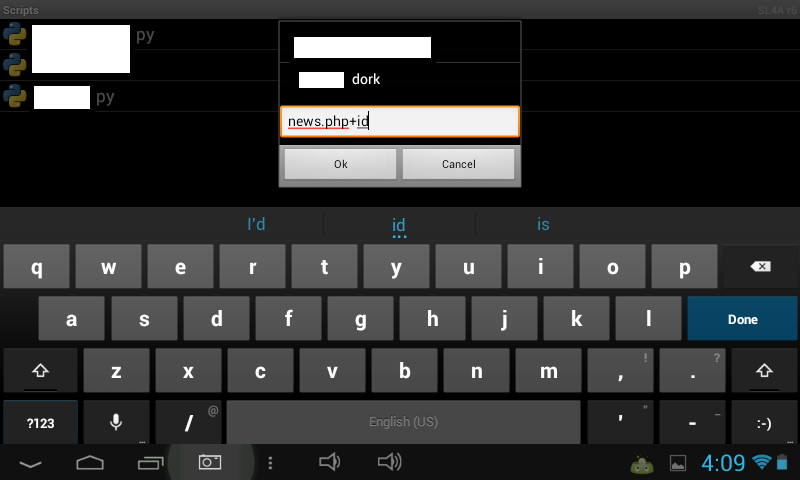
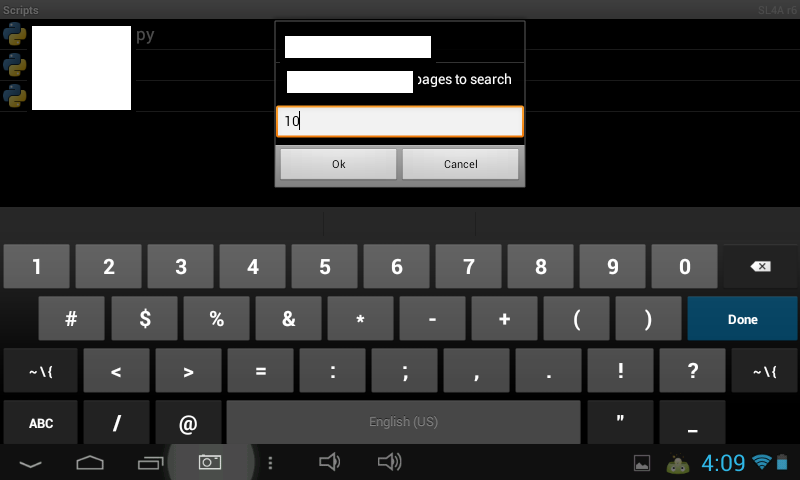
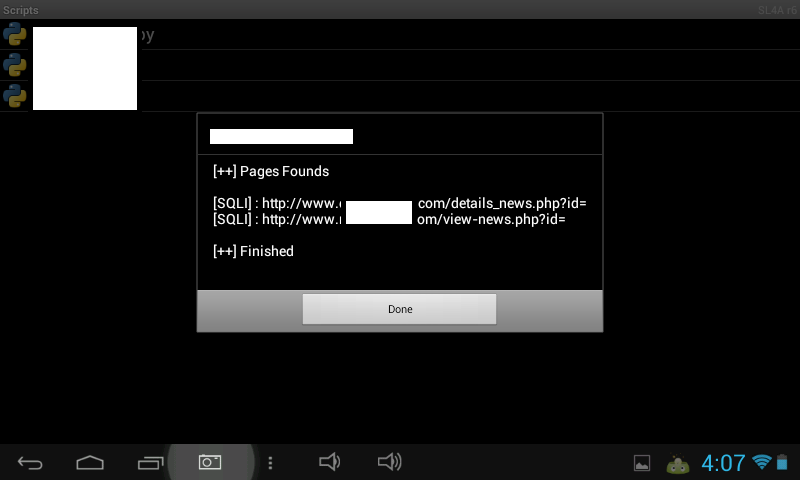 In its current form, the tool isn’t capable of causing widespread
damage, due to the fact that it doesn’t come with a pre-defined database
of dorks for cybercriminals to take advantage of. Therefore, taking
into consideration the fact that they’d have to manually enter them,
greatly diminishes the tool’s potential for causing widespread damage.
However, now that the source code is publicly obtainable, we believe
that fellow cybercriminals inspired by the initial idea will further add
related features to it, either releasing the modified version for
everyone to take advantage, or monetizing the newly introduced features
by pitching it as a private release.
In its current form, the tool isn’t capable of causing widespread
damage, due to the fact that it doesn’t come with a pre-defined database
of dorks for cybercriminals to take advantage of. Therefore, taking
into consideration the fact that they’d have to manually enter them,
greatly diminishes the tool’s potential for causing widespread damage.
However, now that the source code is publicly obtainable, we believe
that fellow cybercriminals inspired by the initial idea will further add
related features to it, either releasing the modified version for
everyone to take advantage, or monetizing the newly introduced features
by pitching it as a private release.We’ll be naturally monitoring its future development, and post updates as soon as new developments emerge.
No comments:
Post a Comment