In this post, I’ll discuss a commercially available (since 2008) DIY (do it yourself) automatic email account registration tool capable of not just modifying the forwarding feature on some of the email providers it’s targeting, but randomizes the accounting data as well. The tool relies on built-in support for a CAPTCHA-solving API-enabled service, and can also activate POP3 and SMTP on some of these accounts thus making it easier for cybercriminals to start abusing them.
Sample screenshots of the tool in action:
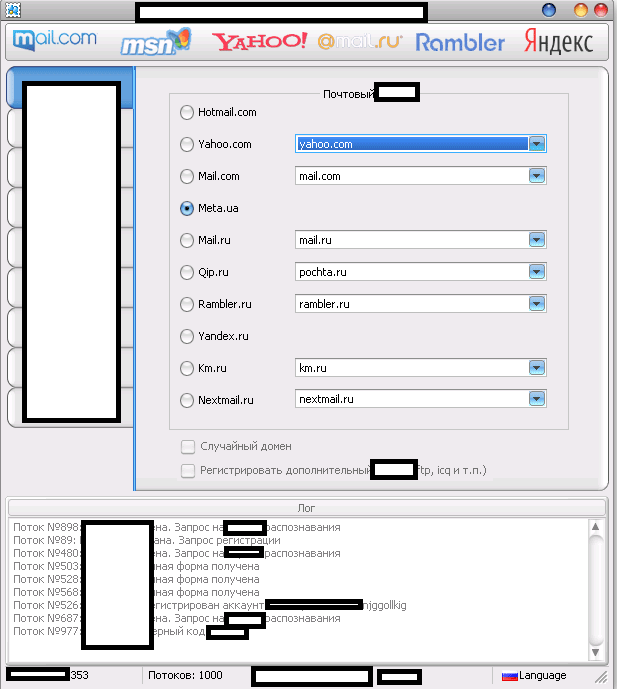
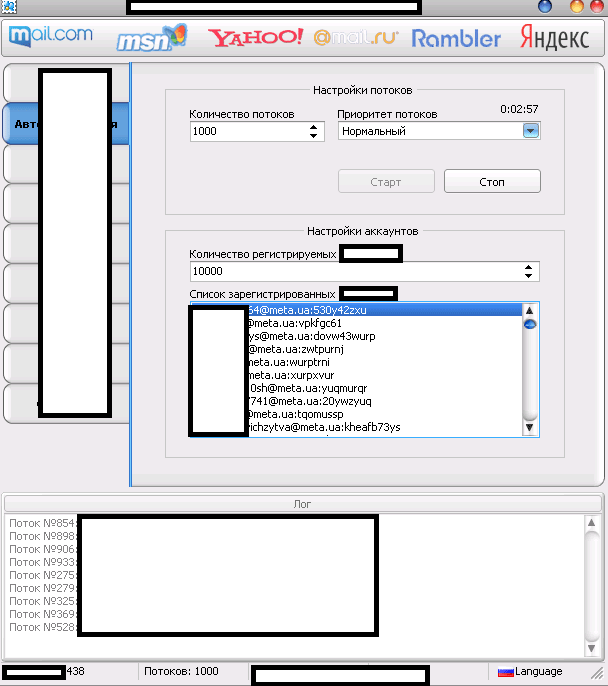
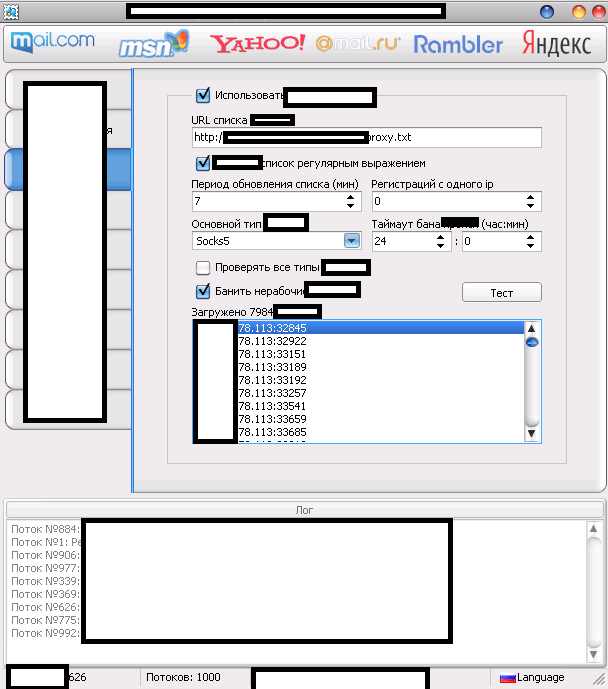
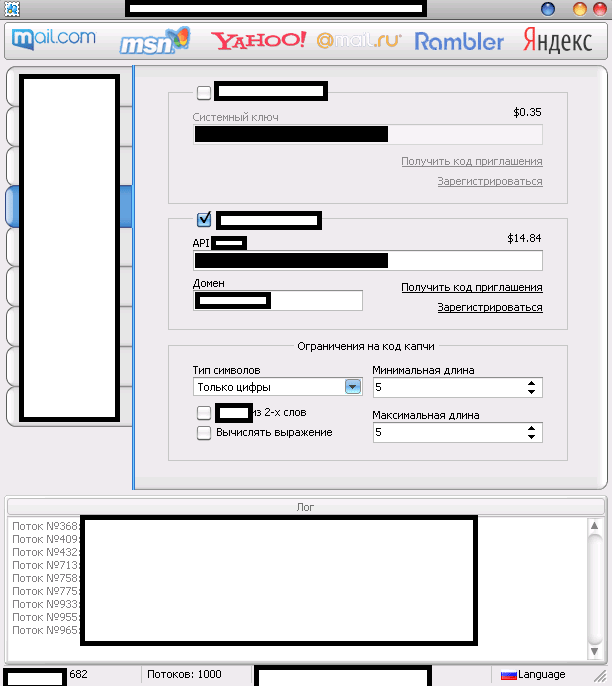
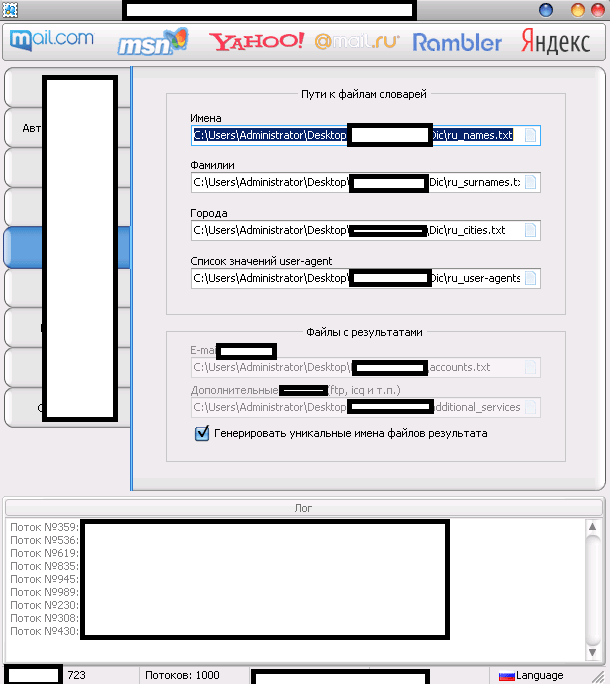
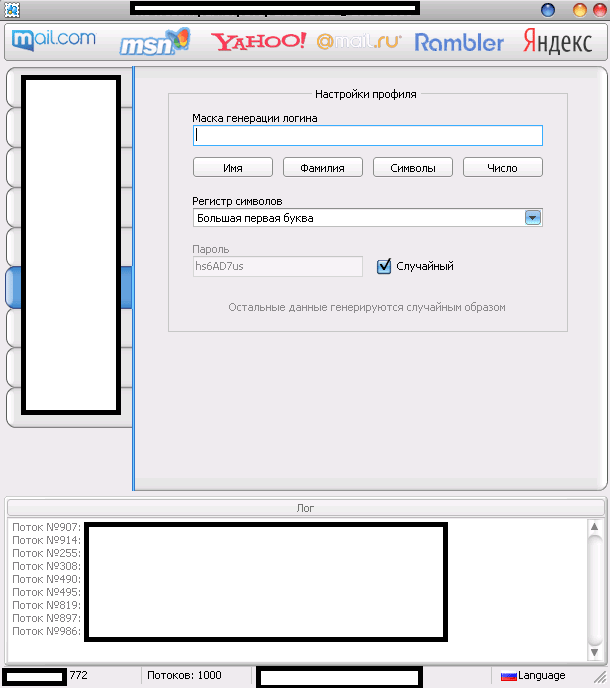
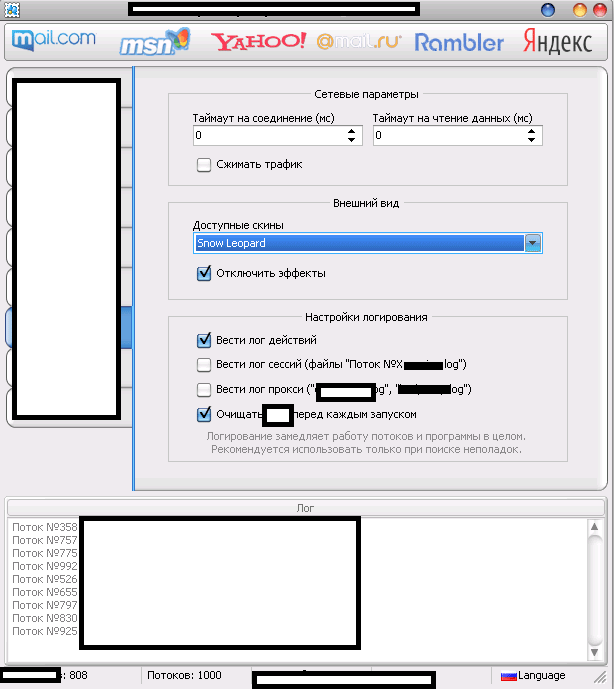
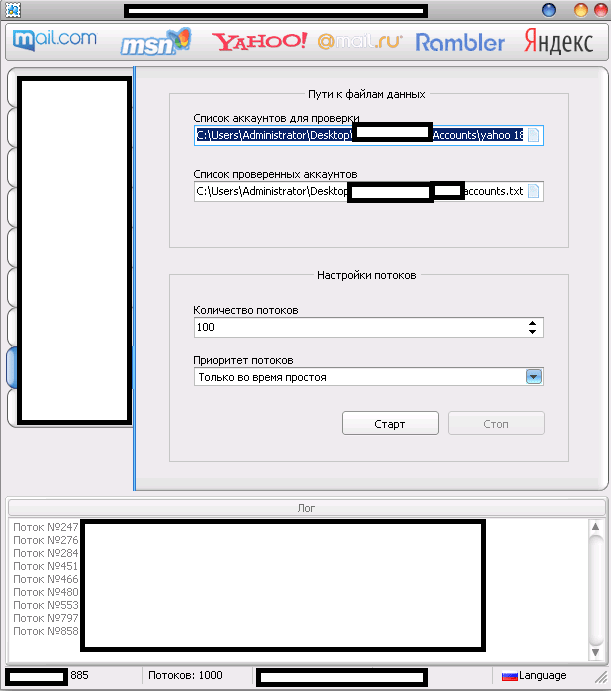
 The multi-threaded tool “naturally” supports direct syndication of “fresh” Socks4/Socks5 malware-infected hosts,
as well as randomization of the user agent, in an attempt by its users
to anonymize their malicious account registration activities. The tool
also has a built-in support for two of the market leading commercial
CAPTCHA-solving services, ensuring that the CAPTCHA challenge will by
successfully bypassed thanks to the introduced API on behalf of these
services.
The multi-threaded tool “naturally” supports direct syndication of “fresh” Socks4/Socks5 malware-infected hosts,
as well as randomization of the user agent, in an attempt by its users
to anonymize their malicious account registration activities. The tool
also has a built-in support for two of the market leading commercial
CAPTCHA-solving services, ensuring that the CAPTCHA challenge will by
successfully bypassed thanks to the introduced API on behalf of these
services.What would a cybercriminal do with all of these automatically registered bogus accounts? Plenty of (fraudulent) options.
- Web-based spam relying on the DomainKeys verified/trusted network infrastructure of the providers – over the years spammers have realized the potential of a DomainKeys trusted (internal) network, and therefore, quickly adapted to its adoption, largely thanks to the demise of CAPTCHA, allowing them to efficiently register hundreds of thousands of rogue accounts to be later on used in spam campaign.
- Automatic activation and abuse of related account services – certain free email service providers, also automatically enable FTP and Web hosting services, allowing the cybercriminals behind the campaign to multi-task by abusing each and every activated service, of course, in an automated fashion, just like the initial account registration process
- Sell access to the bogus accounting data to fellow (novice) cybercriminals – novice cybercriminals look for ways to obtain automatically registered accounts to be later on used as a foundation for their fraudulent campaigns, are the prime market segment targeted by customers of such tools, who take advantage of the fact that novice cybercriminals are still building their capabilities, and remain unaware of the existence of such type of tools, meaning the’d be even willing to pay a premium to get hold of such type of rogue accounts
No comments:
Post a Comment