A newly launched E-shop is currently offering access to hundreds of thousands of compromised legitimate Mail.ru, Yahoo, Instagram, PayPal, Twitter, Livejournal, Origin, Skype, Steam, Facebook, and WordPress accounts, as well as 98,000 accounts at corporate SMTP servers, potentially setting up the foundation for successful spear-phishing campaigns.
Sample screenshot of the inventory of the service:
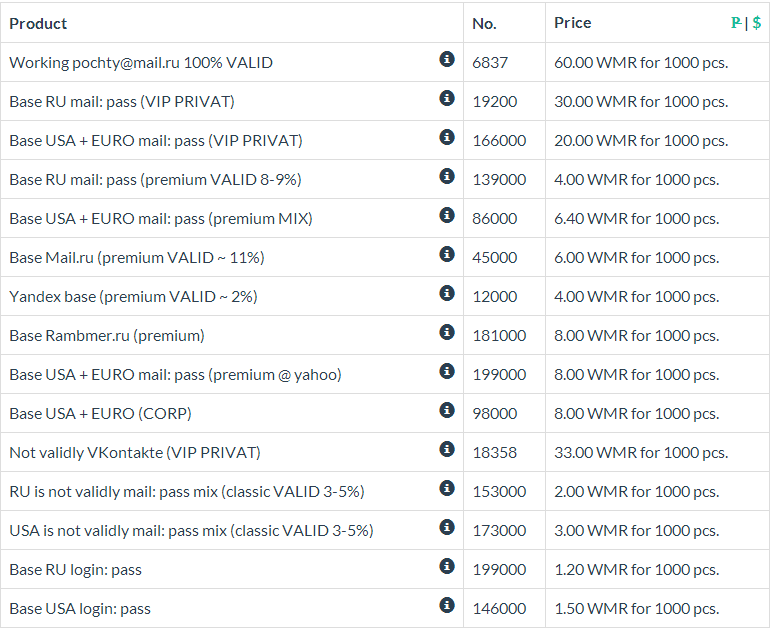 The prices are as follows:
The prices are as follows:- 50, 000 hacked/compromised accounts go for $10
- 100,000 hacked/compromised accounts go for $15
- 500,000 hacked/compromised accounts go for $45
- 1,000,000 hacked/compromised accounts go for $80
- Penetration pricing – penetration pricing is a common pricing technique aimed at quickly gaining market share, and in this particular case, efficiently supplying the stolen assets to potential customers. What’s also worth emphasizing on is that on the majority of occasions, the cybercriminal will automatically ‘break-even’ even if he’s actually invested hard cash into the process of obtaining the hacked/compromised accounting data at a later stage
- Timeliness of a stolen asset in terms of achieving asset liquidity – whether it’s due to the (perceived) oversupply of a particular commoditized underground market item — like for instance compromised accounting data — or the plain simple logic that the fact that it’s been stolen will sooner or later come to the attention of its owner, cybercriminals are no strangers to the concept of achieving financial asset liquidity, and would do their best to reach out to potential customers as quickly as possible
No comments:
Post a Comment