A new commercially available Android, BlackBerry (work in progress) — supporting mobile malware bot is being pitched by its vendor, with a specific emphasis on its potential to undermine modern E-banking security processes, like for instance, SMS alerts. Let’s discuss some of its core features and emphasize on an emerging trend within the cybercrime ecosystem, namely the ‘infiltration’ of Google Play as a service.
Sample screenshots from the mobile malware bot’s manual+the actual administration panel:
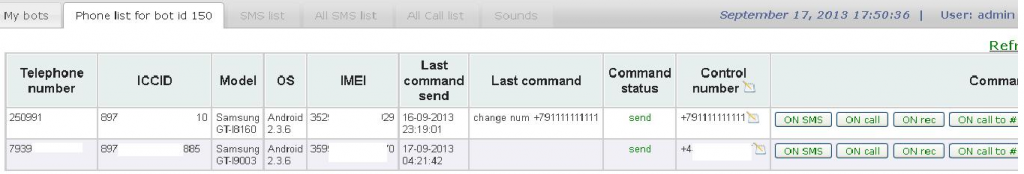

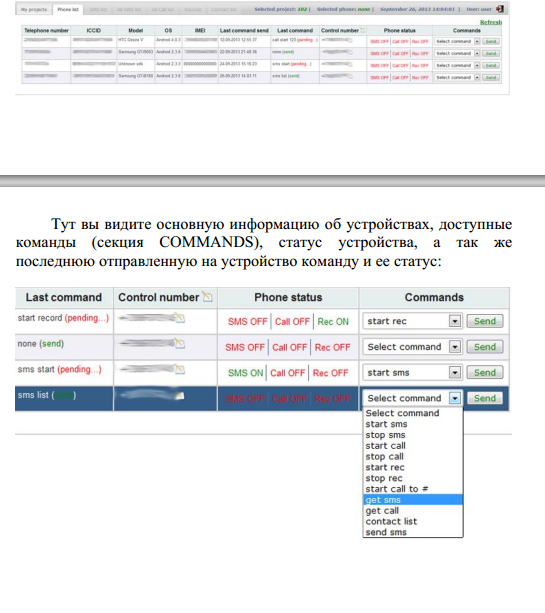
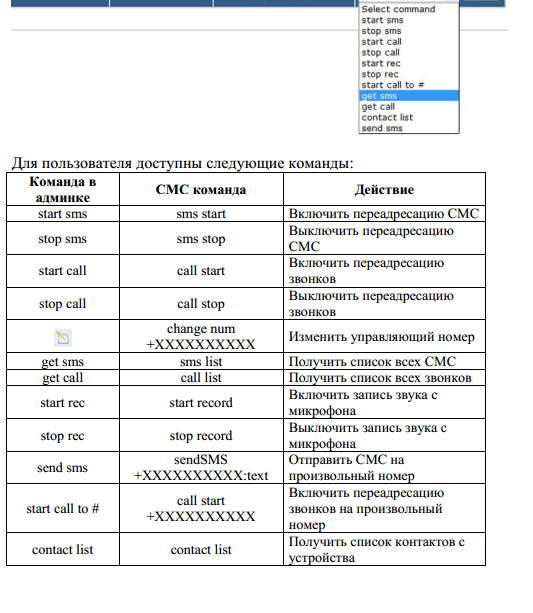
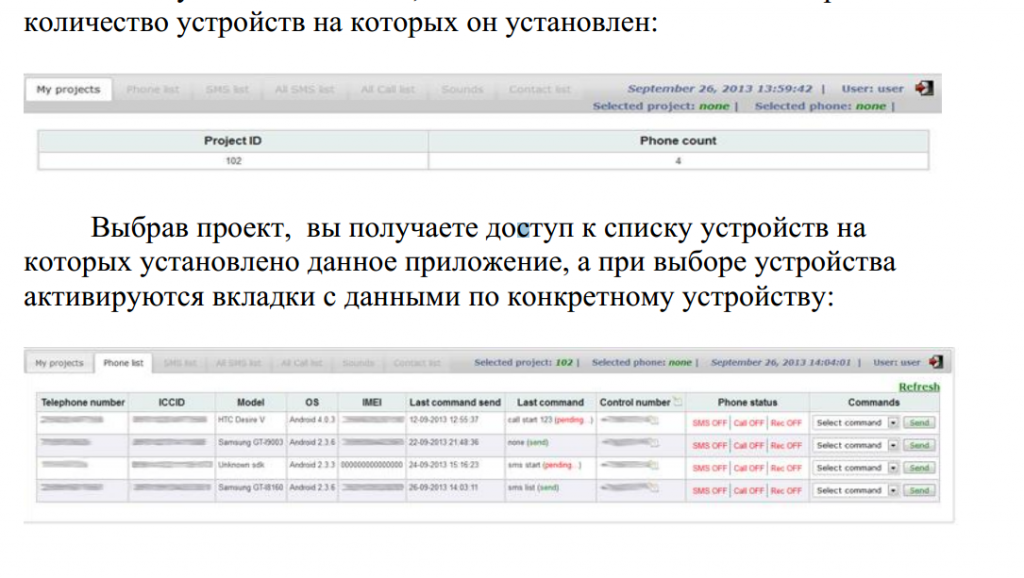
a
 Priced at $4,000, the bot’s features can be used to undermine two factor authentication/SMS
alerts protection features offered by a financial institution, as well
as result in a direct privacy violations once the integrity and
confidentiality of the mobile device has been compromised.
Priced at $4,000, the bot’s features can be used to undermine two factor authentication/SMS
alerts protection features offered by a financial institution, as well
as result in a direct privacy violations once the integrity and
confidentiality of the mobile device has been compromised.Some of the bot’s core features include:
- hijack incoming SMS messages and silently forwarding them to any given number in real-time
- hijacking of any incoming calls and silently forwarding them to any given number in real-time
- complete access to the SMS messages on the affected device
- complete access to the Call History of an affected device
- complete access to the Contacts found on an affected device
- audio recording using the device’s microphone, the uploading the file to a server
- sending an SMS on behalf of the infected device’s owner
- call any number of behalf of the infected device’s owner
- control the infected mobile device through an Internet connection, or through SMS messages in cases where no Internet connection is available
- get the phone number, as well as the ICCID, IMEI, IMSI, Model and OS of the infected device
We’ll continue monitoring the development of this mobile malware bot, and post updates as soon as its vendor introduces any features that could continue adapting to current/emerging anti mobile banking fraud processes.
No comments:
Post a Comment