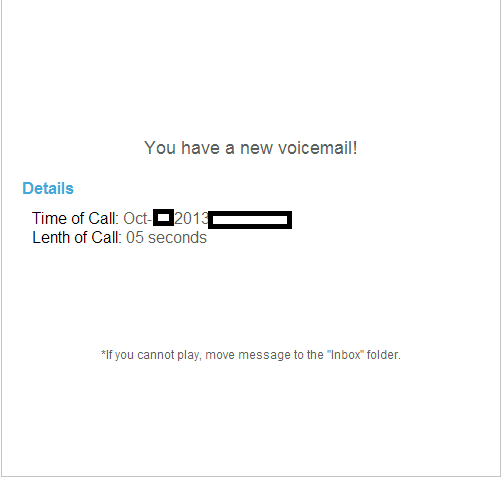
Sample screenshot of the spamvertised email:
 Detection rate for the malicious attachment: MD5: 0458a01e42544eacf00e6f2b39b788e0 – detected by 31 out of 48 antivirus scanners as Trojan.Win32.Sharik.qhd
Detection rate for the malicious attachment: MD5: 0458a01e42544eacf00e6f2b39b788e0 – detected by 31 out of 48 antivirus scanners as Trojan.Win32.Sharik.qhdOnce executed, the sample creates the following Registry Keys on the affected hosts:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.sewwe
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.sewwe\ShellNew
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\DefaultIcon
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\shell
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\shell\open
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\shell\open\command
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\shell\print
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\shell\print\command
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\shell\printto
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\S6.Document\shell\printto\command
HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications
HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications\S6
HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications\S6\Settings
It then attempts to download additional malware from the well known C&C server at networksecurityx.hopto.org
No comments:
Post a Comment