Let’s discuss yet another managed service offering spam-ready SMTP servers, and connect it to malicious campaigns that have directly interacted with the same infrastructure it’s currently hosted on, indicating that it’s already “in business”.
Sample screenshot of the inventory of harvested emails offered by the service:
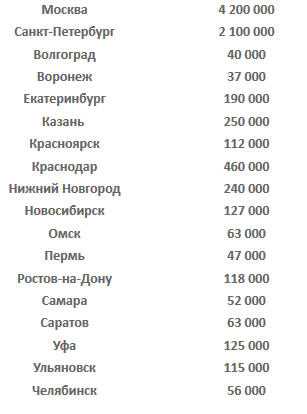 Sample pricing scheme offered by the spam-ready managed SMTP service in Rubles, based on the number of emails to be delivered:
Sample pricing scheme offered by the spam-ready managed SMTP service in Rubles, based on the number of emails to be delivered: Sample screenshot of the pricing scheme for high-volume spam customers on a monthly/yearly basis in Rubles:
Sample screenshot of the pricing scheme for high-volume spam customers on a monthly/yearly basis in Rubles: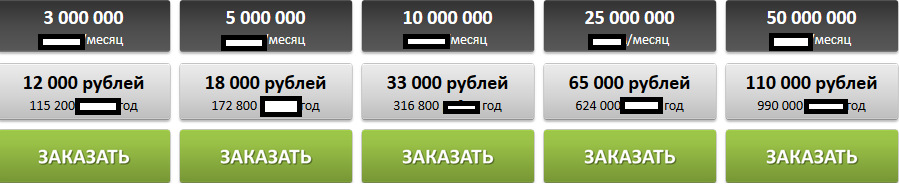 The Web site of the service currently responds to 92.53.125.90, with the same IP known to have been participating in a multiple malicious client-side exploits serving campaigns.
The Web site of the service currently responds to 92.53.125.90, with the same IP known to have been participating in a multiple malicious client-side exploits serving campaigns.Not surprisingly, we can easily correlate malicious/spam activity that’s been taking place through related domain that are known to have been responding to the same IP (92.53.125.90) over the past couple of months.
Known to have responded to the same IP are also the following malicious/fraudulent domains:
1novishop.ru
2353333.ru
3-16.ru
a-kara.ru
aist-letit.ru
akpp-samara.ru
alekseikondratenko.ru
antonagafonov.com
apuzzle.ru
azmarketing.az
barguzin.su
bibcamvids.tmweb.ru
bigbakery.ru
black-panther.ru
blog-net.ru
bloody-knight.ru
bloodyfight.net
bpost.kz
budetsuper.ru
bumblebee.timeweb.ru
We’re also aware of the following malicious MD5s that are known to have directly communicated with the same IP (92.53.125.90) over the last couple of months:
MD5: 7803671e9968000944fd784710c1eefd
MD5: 3619a6ca52c100abce2c0bd8f8b47c4d
MD5: 2dcfa7175ca4585fe2fe5cd2e3df2e4c
MD5: d9d78697efae9f4ab91146926a4c6270
MD5: 86d5218dd28e13d3422d40a774996677
MD5: 437b9b83e1c9c5acabce191622090d57
MD5: 8c935280e432afe193b67de986389e84
MD5: 0ac8272b54dc0c42d62a2e570dde8ee7
MD5: d99399f600b2143167ac3891fa7c2c94
MD5: 1f6a6618d1a5d119f7ebb45f05e76066
MD5: 087cba21e1fdc739e0ff57528be02bcc
MD5: 774c7763a6a0f11628ee7360edb8780e
MD5: 21856c83167d364394beb83474379fea
MD5: af168e2d558167d85ee25afcb1fce46a
In particular the samples have phoned back to the following URLs that are known to have responded to the same IP that the managed SMTP spam service is currently hosted on:
zazaru.com (92.53.125.90)
ckynyagan.ru (92.53.125.90)
pravonapravo.com.ua (92.53.125.90)
ust-jugan.ru (92.53.125.90)
rp.fast-worlds.com (92.53.125.90)
xn—-7sbhbmbrhbip1ajtrecv1fxf.xn--p1ai (92.53.125.90)
srub68.ru (92.53.125.90)
bloodyfight.net (92.53.125.90)
All of these sample establish a UDP communication channel to the following C&C server: 208.115.109.53:8010
How is the actual spamming and acquisition of the spam-ready infrastructure taking place? Through compromised Web sites. Consider going through this assessment of the actual malware used in these campaign courtesy of the fine folks at Abuse.ch.
No comments:
Post a Comment