Let’s take a peek inside the infrastructure ‘facility’, and discuss the vendor’s business model in the over-populated market segment for bulletproof hosting services, currently available to prospective cybercriminals.
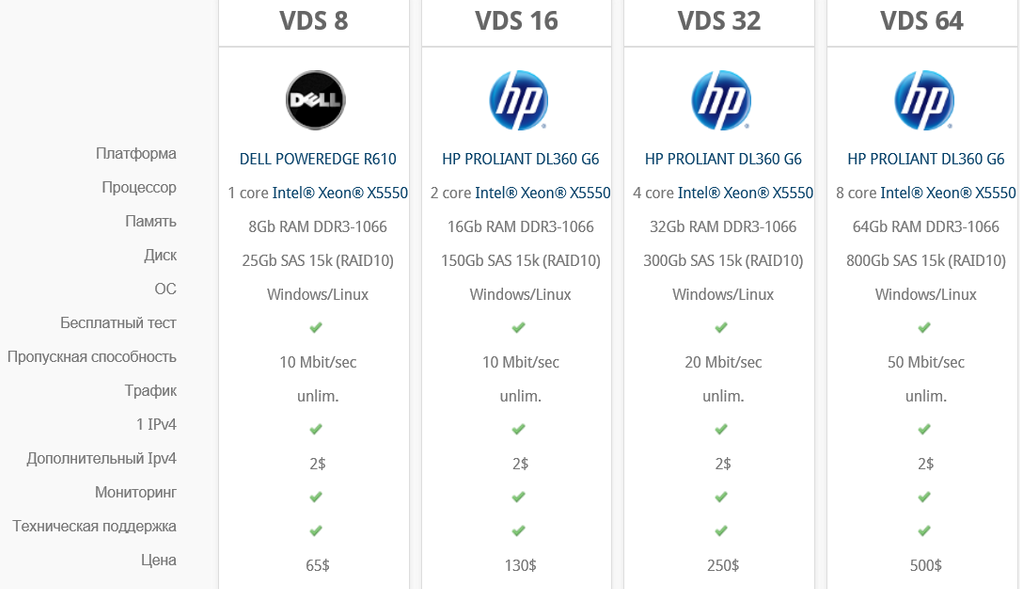
Sample screenshot of the currently offered bulletproof hosting options:
 Sample screenshots of the used HP Smart Arrays in the service’s infrastructure, and the DIY self-monitoring interface:
Sample screenshots of the used HP Smart Arrays in the service’s infrastructure, and the DIY self-monitoring interface: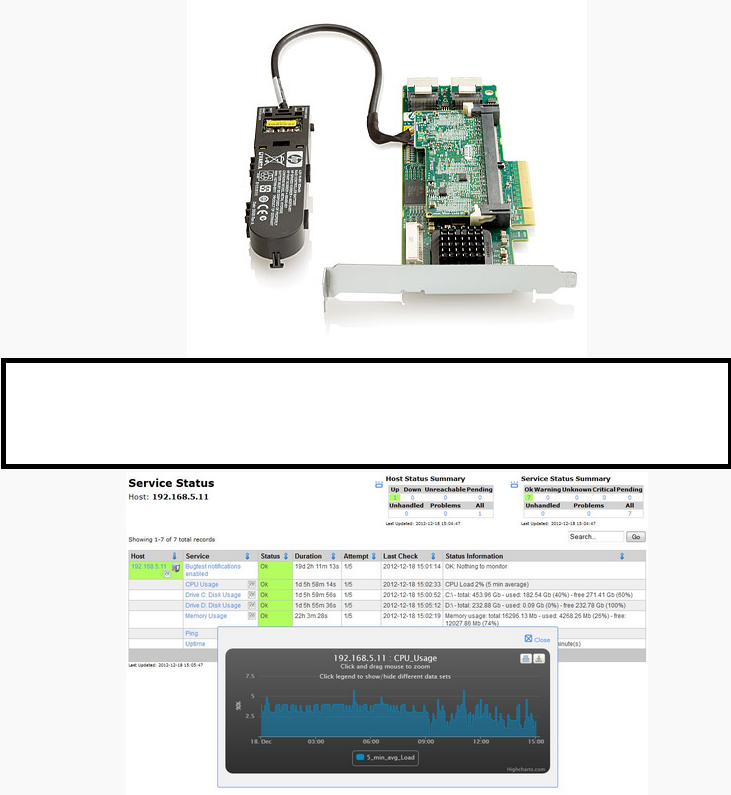 Sample screenshots of the actual infrastructure ‘facility’ as featured by the vendor of the bulletproof hosting service:
Sample screenshots of the actual infrastructure ‘facility’ as featured by the vendor of the bulletproof hosting service:


 This service and its infrastructure are a great example of ‘purely
malicious in-house infrastructure’ purposely set up to facilitate
fraudulent and malicious online activity. The “even if it’s there we
still don’t care” mentality results in a situation where despite the
fact that the vendor’s infrastructure remains online, it can still get
blocked by the industry, consequently preventing hundreds of millions of
users from (unknowingly) interacting with it. Unfortunately, as we’ve
already seen in previous cybercrime-friendly ISP shut downs, this
doesn’t really present a problem to the cybercriminals operating it,
thanks to the contingency planning in place, allowing them to quickly
restore service to their customers.
This service and its infrastructure are a great example of ‘purely
malicious in-house infrastructure’ purposely set up to facilitate
fraudulent and malicious online activity. The “even if it’s there we
still don’t care” mentality results in a situation where despite the
fact that the vendor’s infrastructure remains online, it can still get
blocked by the industry, consequently preventing hundreds of millions of
users from (unknowingly) interacting with it. Unfortunately, as we’ve
already seen in previous cybercrime-friendly ISP shut downs, this
doesn’t really present a problem to the cybercriminals operating it,
thanks to the contingency planning in place, allowing them to quickly
restore service to their customers.In retrospect: How cybercrime-friendly ISPs got affected by successful take downs over the years:
We’ll continue monitoring this market segment, and post analyses of newly launched/competing services, in particular the ones differentiating their UVP (unique value proposition) to prospective cybercriminals.
No comments:
Post a Comment