The majority of financial service professionals considers Man In The
Browser as the greatest threat to online banking, cybercrime increases
its use.
Man In The Browser attack,
DDoS attacks,
phishing
are most insidious cyber threats against banking institutions. Last
statistics proposed by principal security firms confirm that online
banking is considered a lucrative business for
cybercrime.
The large diffusion of online banking platforms, their openness to mobile and
social networking
platforms are attracting the attention of cyber-criminals that are
concentrating their effort against online banking services. The first
form of attacks was considered phishing, using social engineering tricks
crocks are able to obtain banking credentials from unaware banking
customers.
Unfortunately also malware authors concentrated their efforts to hit
the growing sector developing new malicious code able to steal banking
credentials from victims often including key-loggers agent and screen
grabbing modules.
The response of banking world was the improvement of
authentication processes,
a classic example is represented by rapid diffusion for multi-factor
authentication such as OTPs (e.g. One-time passwords device/service
(SMS, email), a hardware token).
The cybercrime ecosystem has widely used the man-in-the-browser
attacks to overtake defense systems, let’s see what it is and which are
the countermeasure that could be really effective for user’s security.
The majority of financial institutions in numerous surveys has
considered Man In The Browser as the greatest threat to online banking.
In the classic scheme for the “
Man in the Middle”
attack the attacker lies between the victim client and the banking
server, it’s clear that the introduction of encrypting traffic could
make ineffective the technique.
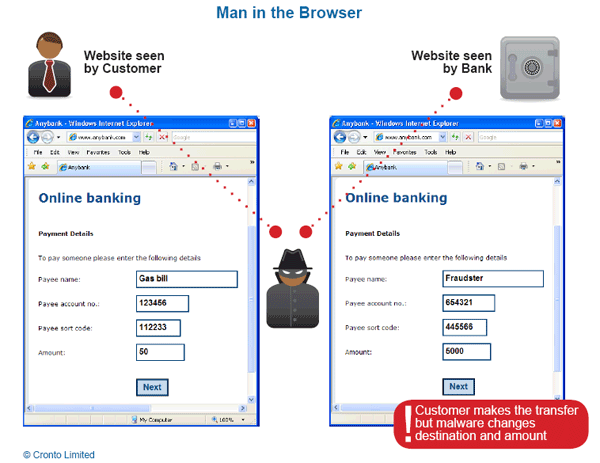
In the Man-in-the-browser schema the attackers integrate the concept
proper of the above methods with the use of malicious code that infects
victims client component such as the browser. Usually MITB appears in
the
form of BHO (Browser Helper Object
)/Active-X Controls/Browser Extension/Add-on/Plugin/ API – Hooking.
Man-in-the-browser attack is based on the presence on the victim
machine of a proxy malware that infects the user’s browser exploiting
its vulnerabilities. The malware is able to modify transaction content
or conduct operations for the victims in a completely covert fashion.
The malware is usually able to hide its transactions to the client
altering the content proposed by the browser.
The malware is able to bypass multi-factor authentication, once the
bank website authenticates the user that has provided the correct
credentials the Trojan horse waits for the transactions to modify its
content. The malicious code is also able to provide evidence of the
success of the user’s transaction altering the content displayed by the
browsers once executed.
The Man In The Browser attack is a very insidious because neither the
bank nor the user can detect it, despite a multifactor authentication
process,
CAPTCHA
or other forms of challenge response authentication are
implemented. Security experts find that most Internet users (73%) cannot
distinguish between real and fake pop up warning messages neither have
possibility to distinguish malware crafted content.
The majority of financial service professionals in a survey
considered Man In The Browser to be the greatest threat to online
banking, malware such as
Zeus,
Carberp, Sinowal and Clampi have inbuilt MITB capabilities. Recently a Trusteer’s security team identified a new instance of the
Ramnit malware that uses the
HTML injection to target the digital distribution platform for online gaming Steam.
Unfortunate end-users
are
still vulnerable to Man In The Browser attacks, their unique
responsibility it to try to limit the occasions of exposure to attacks
(e.g. Phishing) that could allow the infection of their system.
The most efficient countermeasure is considered out of Band
transaction verification containing transaction details along with OTP
and on bank side the adoption of a Fraud detection based on User
behavior profiling.
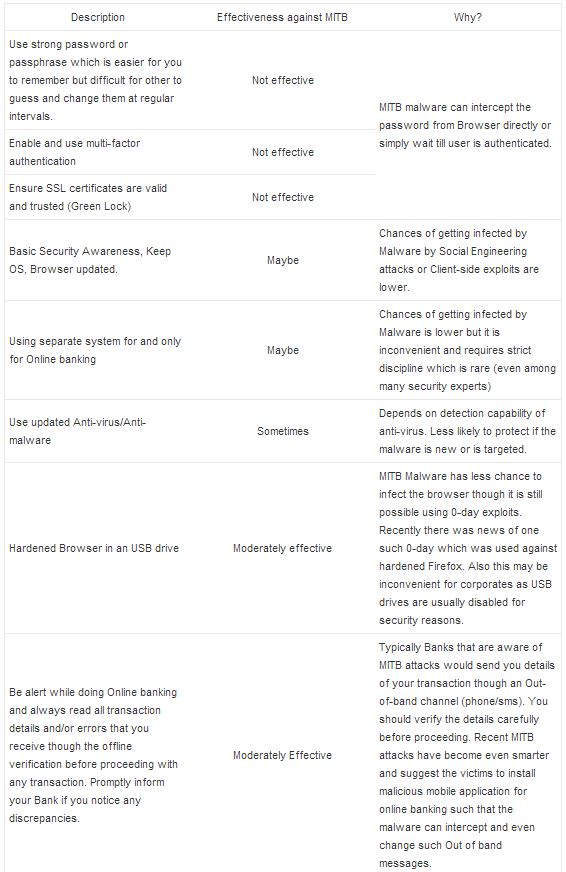
In the following table a useful table that resume principal
countermeasures adopted against a Man-in-the-browser attack and their
real effectiveness.