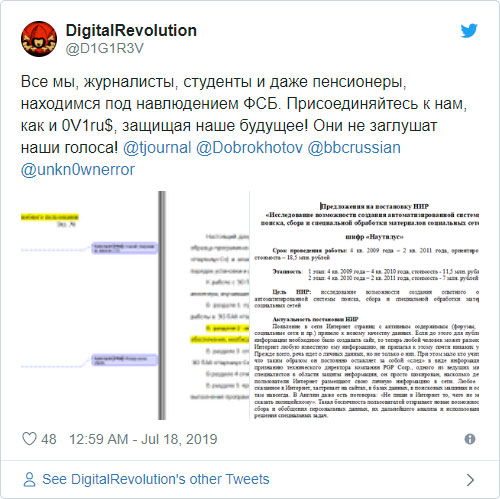
A contractor for the Russian Federal Security Service (FSB) has been hacked and secret projects that were being developed for the intelligence agency were leaked to Russian Media. These projects detail Russia's attempt to de-anonymize users on the Tor network, collect data from social networks, and how to isolate the Russian portion of the Internet from the rest of the world.
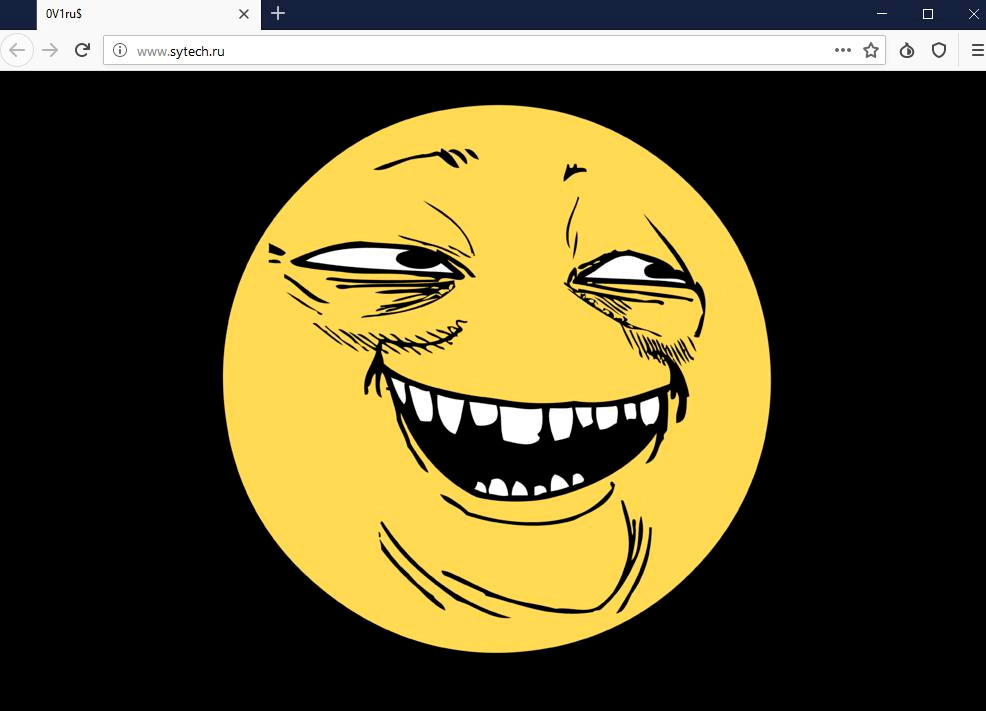
On July 13th, 2019, a contactor for the Russia FSB named "Sytech" was claimed to be hacked by a hacking group named 0v1ru$. As part of this hack, the group defaced the contactor's site to show an image of "Yoba-face", which they posted an image of on their Twitter feed.
In addition, BBC Russia reports that the hackers stole 7.5TB of data from the contractor's network. This data includes information about numerous non-public projects that were being developed by Sytech on behalf of the Russian government and its intelligence agency.
To prove they gained access to Sytech's servers, 0v1ru$ posted images of internal pages of Sytech's web site and of server drives and users in their Windows domain controller.
This stolen data was then passed on to another hacking group named DigitalRevolution, who shared the data with Russian media. Digital Revolution claimed to have hacked the Russian research institute "Kvant" in 2018.
The stolen data seen by BBC Russia outlines a variety of projects being developed by Sytech. These projects include:
Mentor was allegedly being developed for the Russian military unit No. 71330, which is reportedly the radio-electronic intelligence of the FSB of Russia. This project would monitor selected email accounts at specified intervals in order to collect information related to certain phrases.
Nadezhda, or Hope in English, is a project designed to visualize how Russia is connected to the rest of the Internet. This research is part of Russia's attempts to create a "sovereign Internet" where Russia can isolate itself from the rest of the Internet.
Nautilus is a project developed between 2009 and 2010 to collect information about users on social networks such as Facebook, LinkedIn, and MySpace.
Nautilus-S is research into de-anonymizing users on the Tor network by creating exit nodes that were controlled by the Russian government. This project was allegedly started at the request of the Russian Research Institute "Kvant".
Reward was being designed to penetrate and perform covert operations on peer-to-peer networks. This includes BitTorrent, Jabber, OpenFT, and ED2K
Tax-3 is the most recent project and was commissioned by "Chief Scientific Innovation Innovation Center JSC, reporting to the Federal Tax Service.". This project would provide the ability to manually remove information from the Federal Tax Service about people under state protection.
The site for Sytech (www.sytech.ru) has since been shut down and have not responded to inquiries by the BBC.
While this data breach is not nearly as concerning as the Vault 7 WikiLeaks leak of NSA exploits, the BBC has stated that this is the largest data leak in the history of Russian special services.