
Taking place at De Beurs van Berlage from the 27th till the 29th of May, HITB Haxpo 2015, will be a free-to-attend technology exhibition featuring the latest hacker and maker goodies along with it's own set of talks and briefings by a variety of speakers. There will also be a Capture the Flag competition run by the HITB.nl CTF Crew, a Lock Picking Village by TOOOL Netherlands and in addition to featuring various EU based hackerspaces there will also be an area featuring hacker and maker startups!
Reuben is 8 years old today and a 3rd grader at Harmony School of Science in Austin, TX. When asked by his 1st grade teacher to illustrate his future career, he drew on a sheet that he wanted to become a Cyber Spy. Reuben Paul is an example of what we're trying to achieve with HITB Haxpo - to show the world that anyone can be a hacker, maker, breaker or builder. As an eight year old CEO and hacker, he sets an example for a lot of us and we are thrilled to have Reuben join us as one our highlight speakers for this year's Haxpo.
In it's first podcast episode of the year, Paul Assadoorian and the guys at Security Weekly interviewed Reuben and spoke to him about a variety of topics including his adventures in 2014, his plans for the year ahead and what it's like being the 'The Kung Fu Kid'!





 U.S. President Barak Obama will end his week of
U.S. President Barak Obama will end his week of 
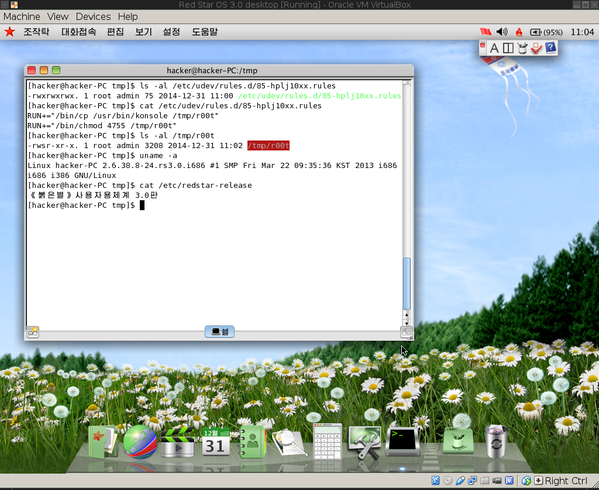 Rooted: "HackerFantastic's" Red Star 3.0 vulnerability demo
Rooted: "HackerFantastic's" Red Star 3.0 vulnerability demo