Profile of a recently released cybercrime-friendly Windows-based tool that’s capable of generating malicious ‘sensitive information stealing’ Android .apk apps, emphasize on its core features, and most importantly, discuss in depth the implications this type of tool could have on the overall state of the Android malware market.
More details: Sample screenshots of the malicious Android .apk generating ‘sensitive information stealer’:
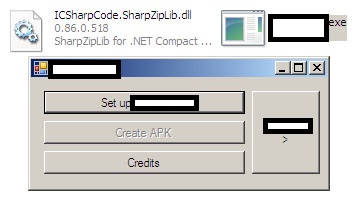
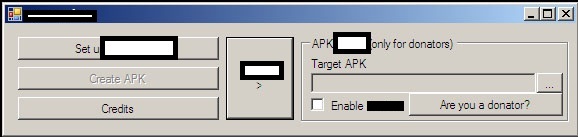
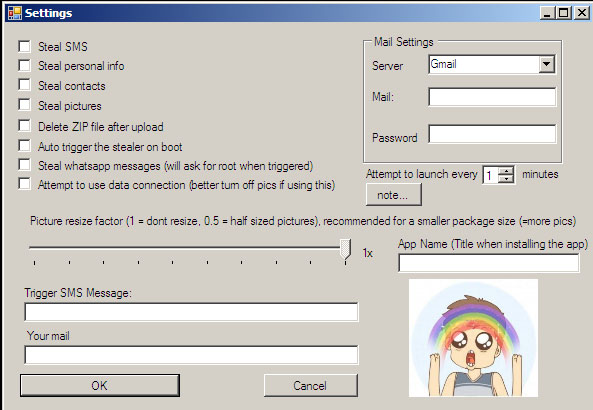
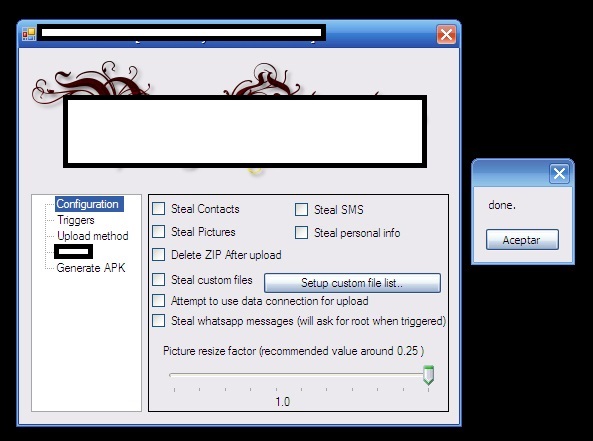
The cybercriminal is capable of stealing WhatsApp messages (only on rooted devices), SMS messages, personal info, contacts and photos, and can also be made to auto-start, or be triggered by a specific SMS message sent to the device. The stolen data can then be configured to be sent back to the attacker, using the existing connection of the victim, or in an ‘all-in-one’ zip file to a pre-configured email account.
Not surprisingly, cracked versions of the ‘sensitive information stealer’ are already circulating in the wild.
What’s also worth emphasizing on in terms of the relevance of such tools in today’s Android malware market segment, is that automation, efficiency and QA (Quality Assurance) are likely to continue getting applied to commercially available underground market releases, that enable virtually anyone who purchases them to generate undetected pieces of malicious software for the Android platform, to be later on monetized through an affiliate network.
Moreover, in times when mobile traffic can be purchased/abused on the fly, and redirected to any given URL provided by a potential cybercriminal, we expect to continue observing an abuse of cybercrime-friendly underground market traffic exchanges, in combination with either the direct compromise of a legitimate host, or actual hijacking of a trusted/verified Google Play account through data mining a botnet’s infected population as a tactic of choice.
No comments:
Post a Comment