With the increased public availability of leaked/cracked DIY malware/botnet generating tools, cybercriminals continue practically generating new botnets on the fly, in order to monetize the process by offering access to these very same botnets at a later stage in the botnet generation process. In addition to monetizing the actual process of setting up and hosting the botnet’s C&C (command and control) servers, novice cybercriminals continue selling direct access to their newly generated botnets, empowering other novice cybercriminals with the foundations for further disseminating and later on monetizing other pieces of malicious software, part of their own arsenal of fraudulent/malicious tools.
Let’s discuss one such sample service run by novice cybercriminals, once again targeting cybercriminals, that’s selling direct access to mini botnets generated using what appears to be a cracked version of a popular DIY malware/botnet generating kit, and emphasize on the service’s potential in the broader context of today’s highly professionalized cybercrime ecosystem.
Sample screenshots of the actual (international) underground market proposition:
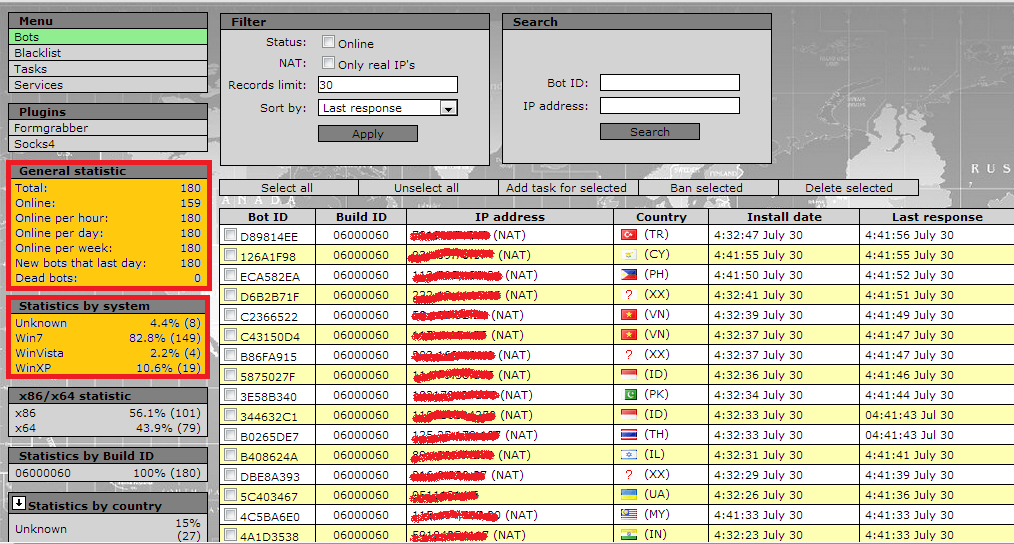
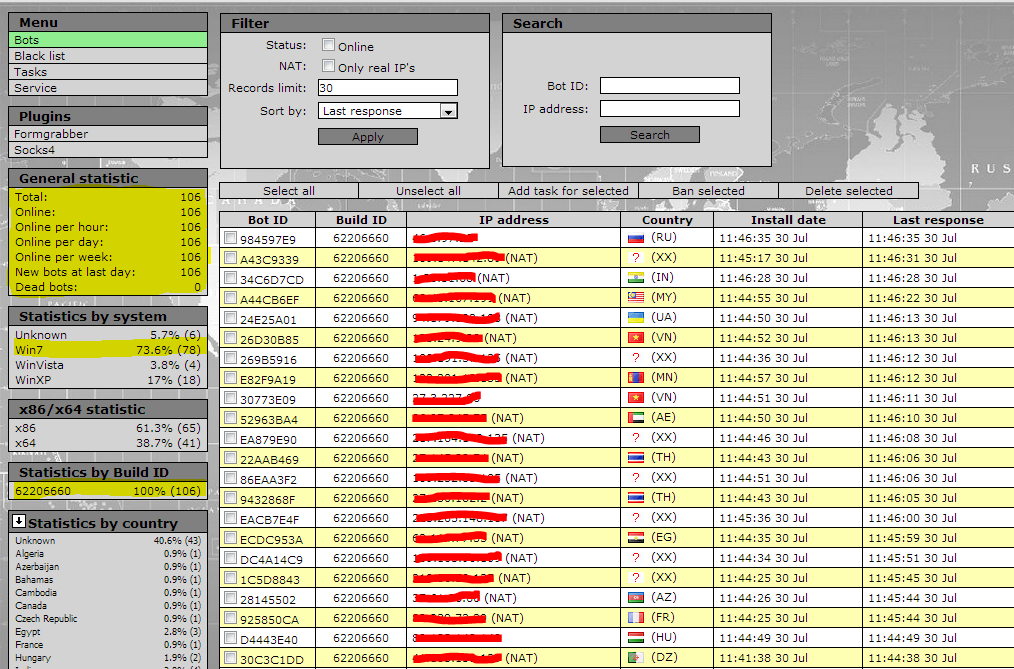
 Sample screenshots of the botnets he’s already sold access to:
Sample screenshots of the botnets he’s already sold access to: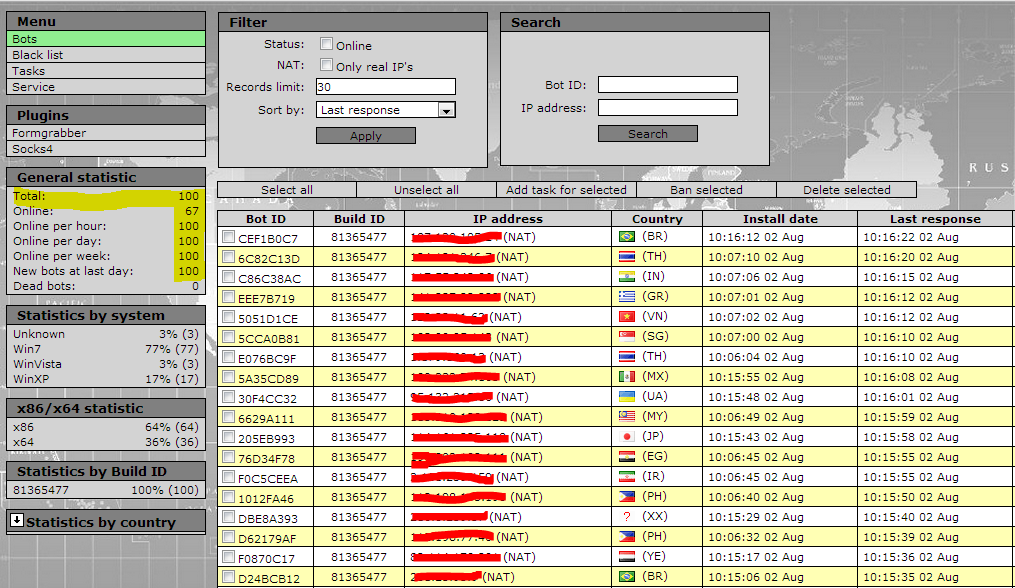
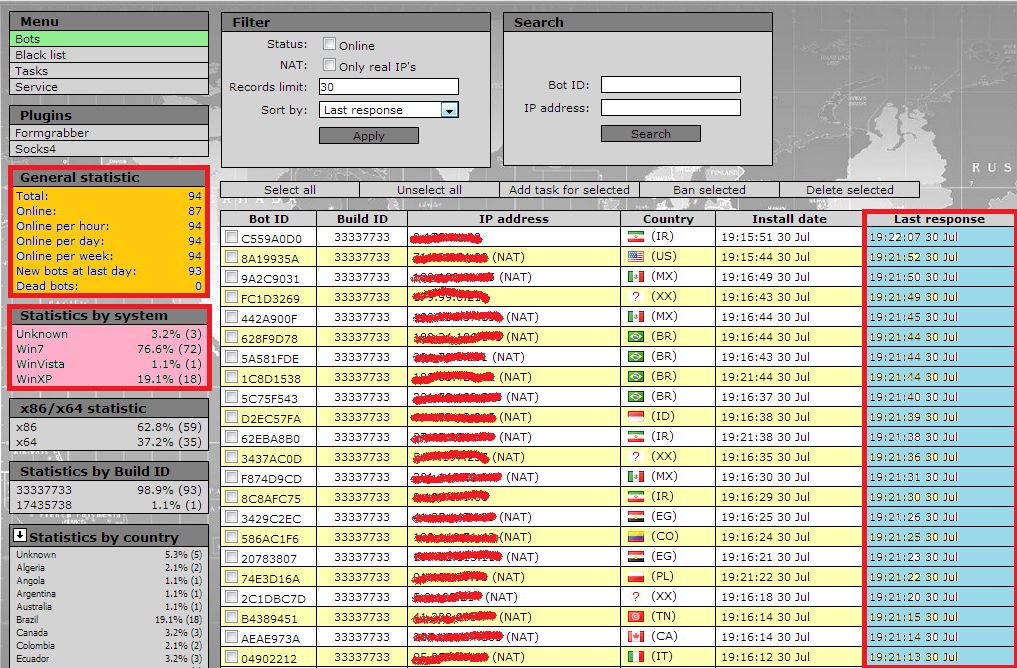
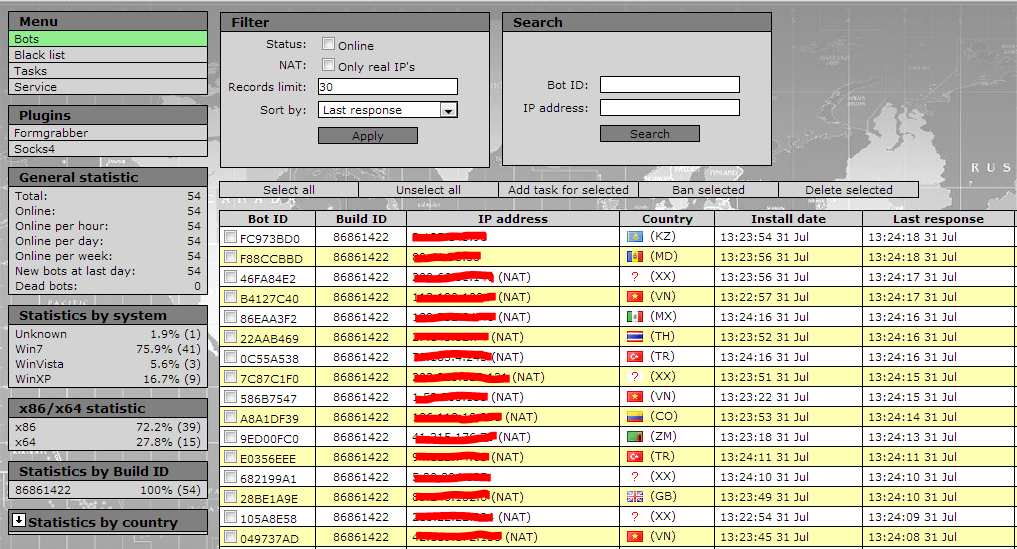 Such (international) underground market services demonstrate the ease of generating and operating beneath the radar
in 2013, where the size of the botnet is proportional with the
(indirectly) applied OPSEC (Operational Security), thanks to the fact
that such mini botnets are usually perceived as smaller threats compared
to sophisticated botnets causing widespread damage on a daily basis.
However, it’s these mini botnets that comprise a huge percentage of the
botnets operated by adversaries launching targeted attacks online, and
it’s only a matter of time before the botnet masters behind them realize
the market potential of geolocated hosts in a specific region/country
of interest to their prospective customers.
Such (international) underground market services demonstrate the ease of generating and operating beneath the radar
in 2013, where the size of the botnet is proportional with the
(indirectly) applied OPSEC (Operational Security), thanks to the fact
that such mini botnets are usually perceived as smaller threats compared
to sophisticated botnets causing widespread damage on a daily basis.
However, it’s these mini botnets that comprise a huge percentage of the
botnets operated by adversaries launching targeted attacks online, and
it’s only a matter of time before the botnet masters behind them realize
the market potential of geolocated hosts in a specific region/country
of interest to their prospective customers.We expect that the novice cybercriminals behind these services will continue capitalizing on the market potential for serving other novice cybercriminals, with their services starting to apply basic QA (Quality Assurance) processes, next to the logical evolution into one-time-stop-E-shops, like the ones we’ve already discussed and profiled in our previous research highlighting some of the current and emerging cybercrime trends in 2013.
No comments:
Post a Comment