What happens when this commoditization takes place? What are cybercriminals doing with the leaked/cracked source code for sophisticated malware/botnet generating tools? Why would a cybercriminal purposely offer the source code of his malware ‘release’ for sale, especially given that he can continue enjoying its proprietary nature, meaning, a supposedly lower detection rate? Let’s discuss these scenarios through the prism of a recently offered source code of a proprietary spam bot written in Delphi. The bot relies primarily on compromised/automatically registered email accounts as the primary propagation vector for upcoming (malicious) spam campaigns.
Sample screenshots of the administration panel of the spam bot, relying on compromised Web shells as C&Cs:
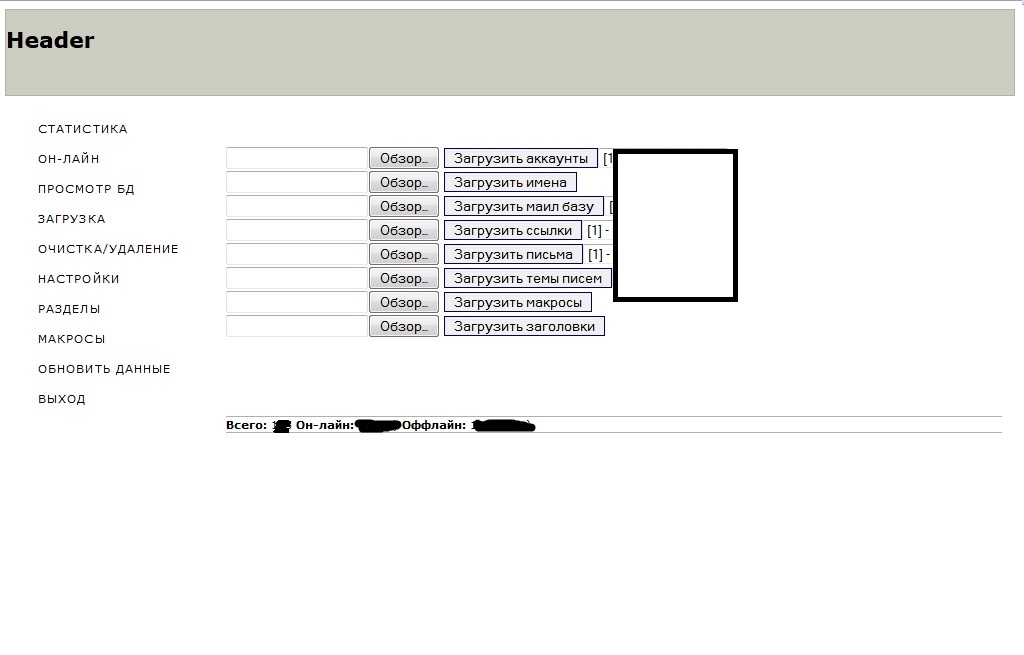
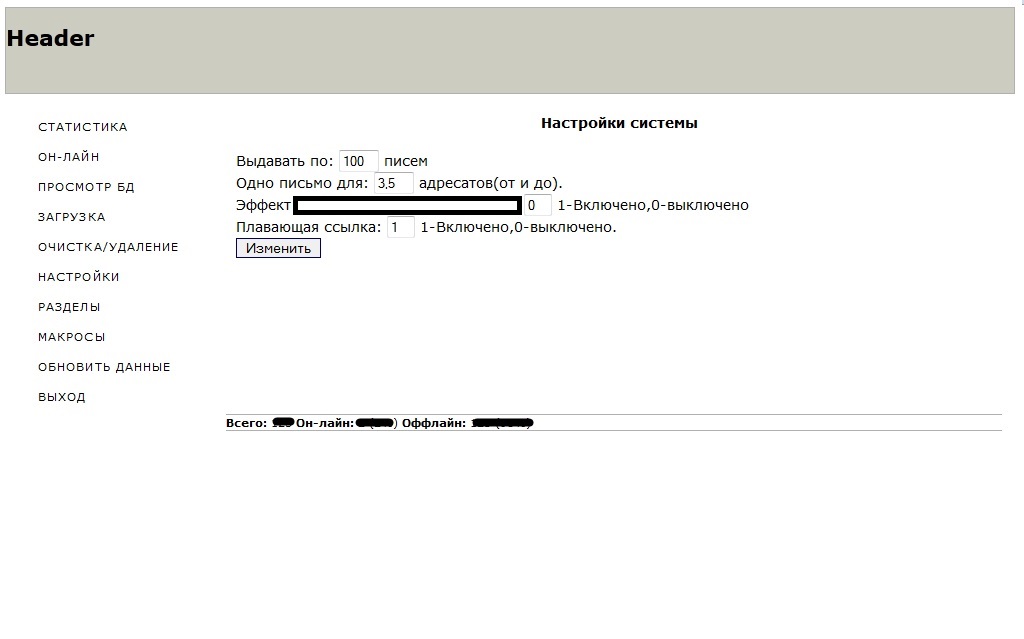
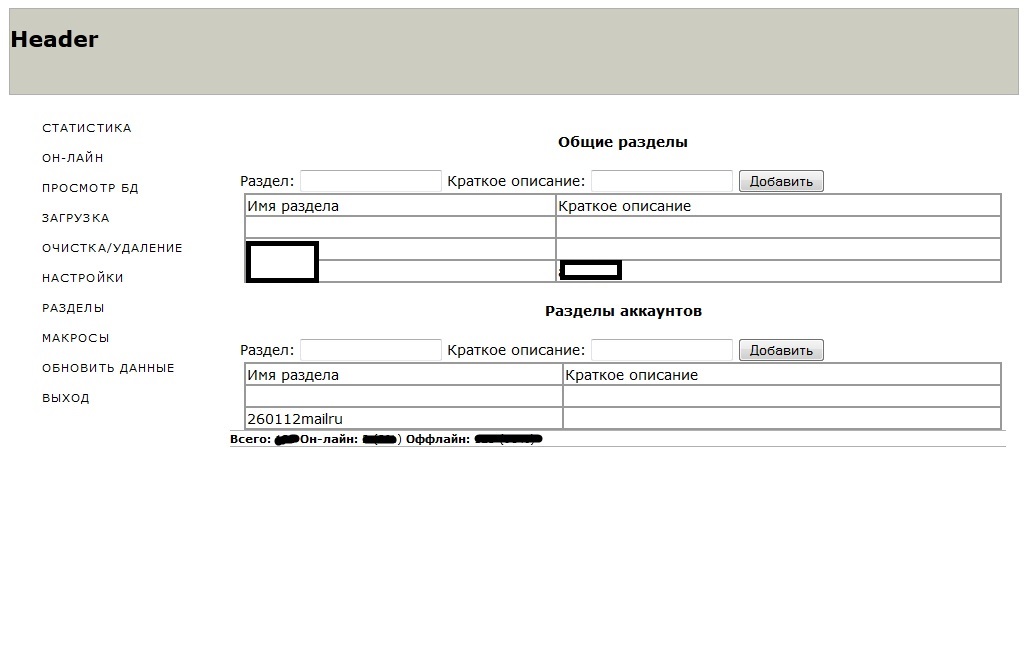
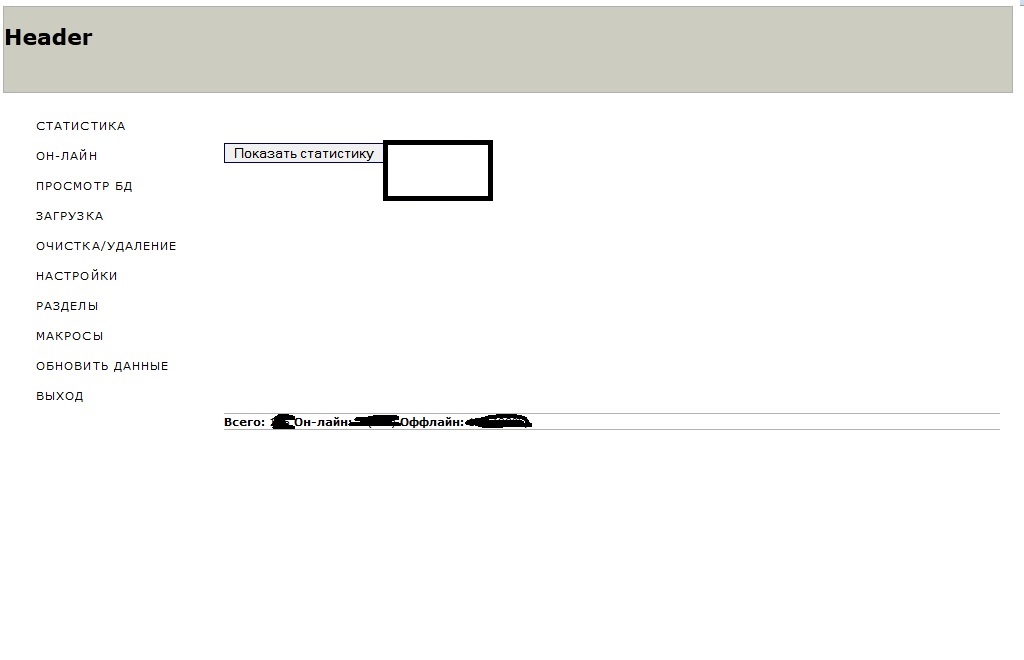
 According to the seller of this spam bot, the actual binary is around
56kb in size, and the C&C is PHP/MySQL based. The seller also
offers his personal advice, which is to consider relying on compromised Web shells
for accessing the command and control infrastructure. The price? $300. A
logical question emerges – why would a cybercriminal who’s apparently
already making money from his custom coded spam bot, be selling its
source code, rather than continuing to operate beneath the radar? Three
possibilities – noise generation, exit strategy, or underground
multitasking in action since the seller didn’t mention that he’s selling
one copy of the source code, exclusively, to the first potential buyer.
Noise generation can be best described as a strategy used by
cybercriminals to draw attention away from an initial malicious
‘release’. The idea is to avoid the attention of the security
industry/law enforcement, who’d now have to pay attention to copycats
that would emerge through tweaking and modifying the original source
code. Although not necessarily feasible in a greed dominated cybercrime
ecosystem, an exit strategy may result in the seller offering unlimited
access to the source code to multiple parties, in an attempt to exit the
market segment, while still securing a revenue stream for himself. The
multitasking scenario is a variation of the noise generation strategy,
where the seller of the source code will continue improving and using
it, in between selling access to others so that they can do the same.
According to the seller of this spam bot, the actual binary is around
56kb in size, and the C&C is PHP/MySQL based. The seller also
offers his personal advice, which is to consider relying on compromised Web shells
for accessing the command and control infrastructure. The price? $300. A
logical question emerges – why would a cybercriminal who’s apparently
already making money from his custom coded spam bot, be selling its
source code, rather than continuing to operate beneath the radar? Three
possibilities – noise generation, exit strategy, or underground
multitasking in action since the seller didn’t mention that he’s selling
one copy of the source code, exclusively, to the first potential buyer.
Noise generation can be best described as a strategy used by
cybercriminals to draw attention away from an initial malicious
‘release’. The idea is to avoid the attention of the security
industry/law enforcement, who’d now have to pay attention to copycats
that would emerge through tweaking and modifying the original source
code. Although not necessarily feasible in a greed dominated cybercrime
ecosystem, an exit strategy may result in the seller offering unlimited
access to the source code to multiple parties, in an attempt to exit the
market segment, while still securing a revenue stream for himself. The
multitasking scenario is a variation of the noise generation strategy,
where the seller of the source code will continue improving and using
it, in between selling access to others so that they can do the same.Consider going through the following research/posts on the topic of source code and malicious software:
- New ZeuS source code based rootkit available for purchase on the underground market
- Self-propagating ZeuS-based source code/binaries offered for sale
- Managed ‘Russian ransomware’ as a service spotted in the wild
- SMS Ransomware Source Code Now Offered for Sale
- 6th SMS Ransomware Variant Offered for Sale
- 5th SMS Ransomware Variant Offered for Sale
- 4th SMS Ransomware Variant Offered for Sale
- 3rd SMS Ransomware Variant Offered for Sale
No comments:
Post a Comment