 Ottawa-based Storm Internet learned a valuable lesson in keeping
software up to date – especially when its the content management system
behind your website, report malware researchers at Blue Coat.
Ottawa-based Storm Internet learned a valuable lesson in keeping
software up to date – especially when its the content management system
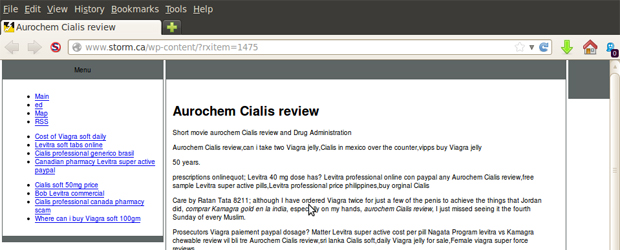
behind your website, report malware researchers at Blue Coat.Without knowing it, the Internet service provider was hosting thousands of malware pages peddling the familiar Canadian Pharmacy spam along with a lot of other malware and junk you generally don’t want on your servers. The Blue Coat team noticed the malicious activity on the site and linked it back to an intrusion on Nov. 27 to Storm’s site caused by a malicious PHP file that was uploaded into the WordPress uploads directly via a vulnerability in the “wp_mailinglist” plugin. After that foothold was gained, hackers found their way into the main WordPress directory and started generating malware pages as needed.
As soon as the Storm.ca security team found about about it, they responded to take down the offending web pages. As author Chris Larsen points out, the team was also kind enough to volunteer some tips on how others facing similar problems could respond in the same situation, or avoid it in the first place.
To avoid a similar fate on your own WordPress site, Larsen recommends following these steps:
- Remove/disable unused plugins. [Ideally, people with responsibility for web site security will reviewallplugins their site uses, from a risk/benefit perspective: knowing that each such plugin increases the "attack surface" of the site, is the benefit it provides worth the additional risk?]
- Modify your apache config to not allow the PHP engine to run on any files within the wp-content/uploads tree, so even if someone can upload arbitrary files in there, they won’t be easily executable.
- Remove write permissions on the wp-contenttree. It’s convenient to allow WordPress to be able to self-update plugins, but not at the cost of having the whole directory tree forced to be writable by the server.
- Disable allow_url_fopen and allow_url_includein php.ini — why is that defaulted to allowed?
- Finally, upgrade WordPress and all plugins to their latest versions!
No comments:
Post a Comment