
The NSA quietly commandeered a botnet targeting US Defence agencies to attack other victims including Chinese and Vietnamese dissidents, Snowden documents reveal.
The allegation is among the latest in a cache of revelations dropped by Der Spiegel that revealed more about the spy agency.
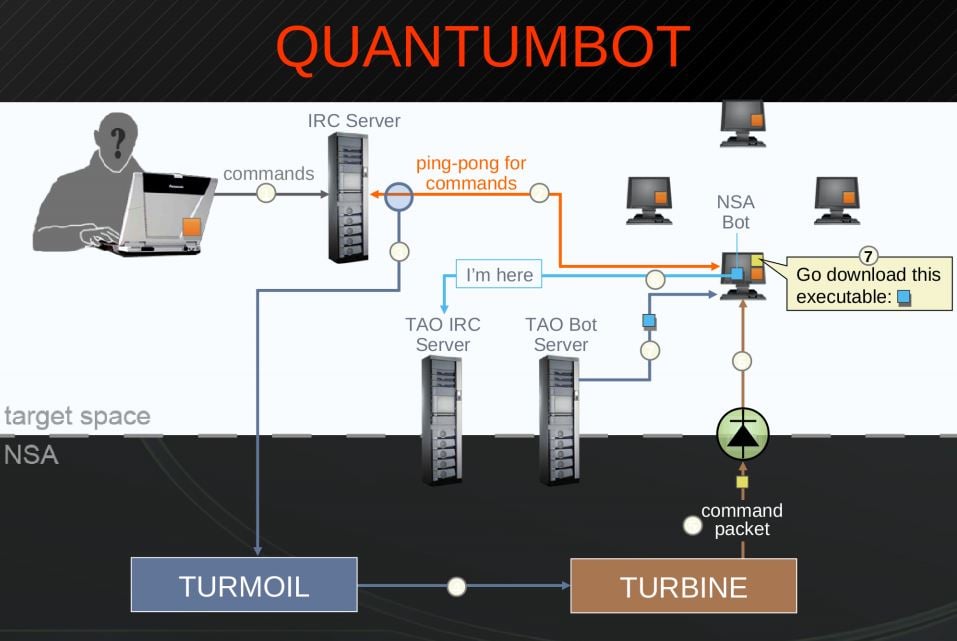
The "Boxingrumble" botnet was detected targeting the Defence Department's Nonsecure Internet Protocol Router Network prompting NSA bods to redirect the attack to a server operated by the Tailored Access Operations unit.
A DNS spoofing attack tricked the botnet into treating the spies as trusted command and control agents. The NSA then used the bot's hooks into other victims to foist its own custom malware.
Much of the bot-hijacking attacks dubbed "Quantumbot" by the NSA was conducted under its operation DEFIANT WARRIOR which utilised XKeyscore and infrastructure of Five Eyes allies including Australia, New Zealand, the UK and Canada to identify foreign bots ripe for attack.
The work granted broader network exploitation, attack and vantage points, NSA Power Point slides revealed (pdf).
It was part of what appeared to be the NSA's dream of having "a botnet upon which the sun never sets", a goal noted under the slide title "if wishes were ponies".
Bots found in the US would be referred to the FBI for cleansing, but infected victims in other countries were considered collateral.
The documents also revealed the NSA's Tutelage program (pdf), a sister to Turmoil and part of the Turbulence family of surveillance and exploitation kit, was used to block distributed denial of service (DoS) attacks by the Anonymous collective.
Tutelage was successful in identifying and blocking internet protocol addresses linked to the Low Orbit Ion Cannon DDoS software when US Defence agencies were attacked.
The documents also revealed NSA spies at Remote Operations Centres exfiltrated data through compromised machines owned by innocent victims that the agency dubbed 'Scapegoat Targets'.
The theme continued under its mobile phone infection efforts designed to plunder data from businesses. Staffers with NSA-infected handsets were referred to as "unwitting data mules", a nod to drug-dealer slang.
No comments:
Post a Comment