beauty products chain Sally Beauty appears to be the latest victim of a breach targeting their payment systems in stores, according to both sources in the banking industry and new raw data from underground cybercrime shops that traffic in stolen credit and debit cards.
On March 2, a fresh batch of 282,000 stolen credit and debit cards went on sale in a popular underground crime store. Three different banks contacted by KrebsOnSecurity made targeted purchases from this store, buying back cards they had previously issued to customers.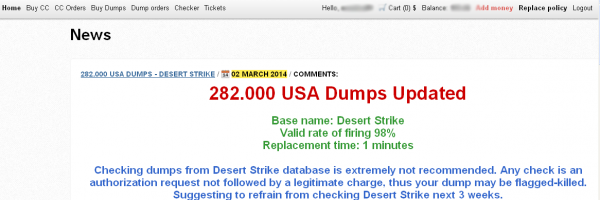
The
card shop Rescator advertising a new batch of cards. 15 cards purchased
by banks from this batch all were found to have been recently used at
Sally Beauty stores.
Each bank independently reported that all of the cards (15 in total) had been used within the last ten days at Sally Beauty locations across the United States. Denton, Texas-based Sally Beauty maintains some 2,600 stores, and the company has stores in every U.S. state.
Asked about the banks’ findings, Sally Beauty spokeswoman Karen Fugate said the company recently detected an intrusion into its network, but that neither the company’s information technology experts nor an outside forensics firm could find evidence that customer card data had been stolen from the company’s systems.
Fugate said Sally Beauty uses an intrusion detection product called Tripwire, and that a couple of weeks ago — around Feb. 24 — Tripwire detected activity. Unlike other products that try to detect intrusions based on odd or anomalous network traffic, Tripwire fires off alerts if it detects that certain key system files have been modified.
In response to the Tripwire alert, Fugate said, the company’s information technology department “shut down all external communications” and began an investigation. That included bringing in Verizon Enterprise Solutions, a company often hired to help businesses respond to cyber intrusions.
“Since [Verizon's] involvement, which has included a deconstruction of the methods used, an examination of network traffic, all our logs and all potentially accessed servers, we found no evidence that any data got out of our stores,” Fugate said. “But our investigation continues, of course with their assistance.”
In any case, the stolen cards mapping back to Sally Beauty appear to have been pilfered quite recently, roughly matching the intrusion timeline noted by Sally Beauty: All of the banks reported fraud occurring on cards shortly after they were used at Sally Beauty, in the final week of February and early March.
The advertisement produced by the criminals who are selling these cards also holds some clues about the timing of the breach. Stolen cards fetch quite high prices when they are first put on the market, but those prices tend to fall as a greater percentage of the batch come back as declined or canceled by the issuing banks. Thus, the “valid rate” advertised by the fraudsters selling these cards acts as an indicator of the recency of the breach, because as more banks begin noticing fraud associated with a particular merchant, many will begin proactively canceling any cards used at the suspected breached merchant.
In this batch of cards apparently associated with the Sally Beauty breach, for example, the thieves are advertising the cards as “98 percent valid,” meaning that if a buyer were to purchase 100 cards from the store, he could expect that all but two would still be valid.
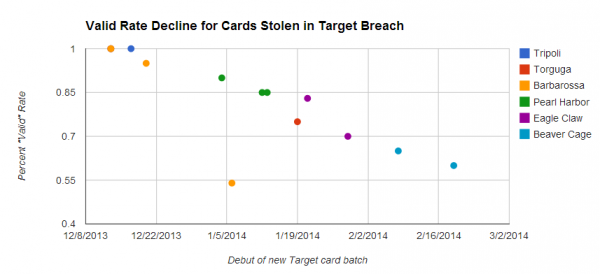
Cards stolen in the Target breach have become much cheaper as more of them come back declined or cancelled by issuing banks.
The items for sale are not cards, per se, but instead data copied from the magnetic strip on the backs of credit cards. Armed with this information, thieves can simply re-encode the data onto new plastic and then use the counterfeit cards to buy high-priced items at big box stores, goods that can be quickly resold for cash (think iPads and gift cards, for example).
Interestingly, this batch of stolen card data was put up for sale three days ago by an archipelago of fraud shops that is closely affiliated with the Target breach. In my previous sleuthing, I reported that a miscreant using the nickname Rescator (and an online card shop by the same name) was among the first — if not the first — to openly sell cards stolen in the Target breach. Further tying the Target breach to Rescator, forensic investigators also found the text string “Rescator” buried in the guts of the malware that was found on Target’s systems. According to additional reporting by this author, Rescator may be affiliated with an individual in Odessa, Ukraine.
No comments:
Post a Comment